This is Part 1 of the Weekend Wrap-Up, detailing significant Threat Actor Activity and noteworthy TTP changes to be aware of.
Part 2 will cover significant vulnerabilities from the past week, in addition to the latest tools & techniques for offense and defence alike, and some additional reporting that you might find relevant and useful.
Headline Items
A rootkit used by DPRK’s Lazarus Group abuses vulnerable kernel drivers to disable security monitoring features throughout the system, blinding AV and EDR products;
Major Australian telco Optus loses sensitive PII for 11.2 million customers through an exposed unauthenticated API. Lapsus$ blamed for Uber & Rockstar hacks, with an arrest made in the UK;
Red Teamers rejoice - this week saw numerous posts on attacking Azure Conditional Access and Pass-through-Authentication; Kerberos FAST, relaying YubiKey authentication, and more. Find those write-ups and more in Part 2!
Lazarus rootkit achieves God-mode with BYOVD attack
Security vendor AhnLab has released a report that takes a deep dive into a rootkit deployed by the North Korean APT Lazarus Group. Their analysis focuses on the use of the Bring-Your-Own-Vulnerable-Driver (BYOVD) technique to drop an vulnerable, legitimate kernel driver to disk, which it exploits to disable all security products on the given system.
Specifically, AhnLab observed the legitimate ene.sys kernel driver from ENE technology being abused, as well as a vulnerability in Dell’s BIOS update utility (CVE-2021-21551) that provided attackers with kernel-level access through use of the ZwWriteVirtualMemory API call. This was used to modify the global kernel data, allowing the attacker to implement a whitelist of only “crucial normal system driver files” - effectively disabling all monitoring mechanisms like Windows Event Tracing (ETW) and the Windows Filtering Platform (WFP) that Antivirus and EDR solutions rely on.
While BYOVD attacks have been observed in numerous times in the recent past and dating as far back as 2014, AhnLab note that through this specific implementation, Lazarus are “the first to design an elaborate rootkit to disable all systems from the old Windows 7 to the most recent OS, Windows Server 2022.”
Mitigations & Detections
Call it fate, but just two days before AhnLab released their report, Elastic shared this fantastic wrap-up on BYOVD attacks, complete with a primer on how it works and 65 YARA rules to get you started in mitigating their use.
They strongly recommend the explicit blocking of known vulnerable drivers in conjunction with Windows Defender Application Control (WDAC), citing the Microsoft recommended driver block rules as a great place to start.
Allow-listing is the next - and much more involved - step in mitigating BYOVD attacks, which may not be feasible for many of the larger organisations out there.
Finally, a favourite of Detection Engineers - looking for behavioural anomalies. Elastic provide an example EQL query that looks for:
Any non-file-deletion event where:
The target file either has the .sys extension or MZ header; and
The process is either not signed or signed by an untrusted authority; and
The driver is loaded via the System Process (ntoskrnl.exe - PID 4).
If BlackCat run Agile - they are crushing their Sprints
Reference: Symantec
Symantec have discovered new versions of the data exfiltration and credential stealer tools being used by the BlackCat ransomware group in recent operations. This follows the creation of an ARM build for their ransomware and safe-mode encryption functionality being added to their Windows build in June this year, and improving their leak site to make stolen data indexed and searchable in July.
Say what you will about the Agile framework, but if BlackCat are running it - you can’t argue with results!
Exmatter - Data Exfiltration
BlackCat’s data exfiltration tool has been actively developed throughout the life of their group, with the latest iteration seeing a huge re-writing of the code base - potentially to mitigate attempts to fingerprint it based on the tool’s features and functionality. Speaking of which - there were a few added and removed:
The dictionary of file types it exfiltrates has been culled significantly;
FTP exfiltration has been added alongside existing SFTP and WebDav options;
Operators can enable a self-destruct option which triggers if executed outside of a non-corporate environment (i.e. non-Windows domain);
SOCKS5 support was removed.
Eamfo - Veeam Credential Stealer
Veeam is a widely used corporate backup solution - as such, it’ll often store credentials that it uses to authenticate to enterprise systems to create backups. Naturally, this includes Domain Controllers, cloud services, and more.
Symantec report they have seen the Eamfo credential stealer used to pilfer creds from Veeam’s back-end SQL database using the following query:
select [user_name],[password],[description] FROM [VeeamBackup].[dbo].[Credentials]
Interestingly, Symantec note that Eamfo has been observed used in attacks deploying the Yanluowang and LockBit ransomware payloads, as well as by the Conti copycat group “Monti”. They further note that GMER - a dated rootkit scanner - has been observed used alongside Eamfo to kill processes during intrusions, and is gaining in popularity across ransomware operations in general.
BlackCat’s active development of their capabilities has helped them to maintain their competitive edge in a market saturated with RaaS programs. Their operation is highly professionalised both in terms of their exclusive affiliate program, and their ransomware’s ability to operate across Windows, ESXi, Debian operating systems, and more.
Keep in mind the fact they use a custom data exfiltration tool - as opposed to LOLBIN-type exfiltration employed by other ransomware crews - and ensure you’re postured to monitor and mitigate attempts to harvest credentials from Veeam SQL databases.
Qakbot TTP Summary
The two Qakbot botnets varied in their initial delivery mechanism, but otherwise adopted the same execution chain that swapped out .bat files for .cmd files to obfuscate the execution of the payload dll, which spawned and injected into Explorer.exe or WerFault.exe
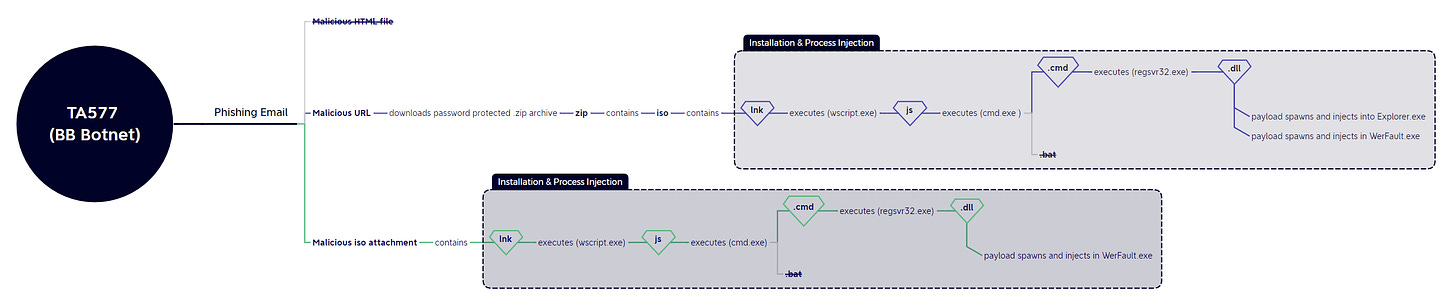
BB Botnet
The main change for the BB botnet (TA577) was the use of .cmd files instead of .bat files used last week, and opting for direct iso delivery or malicious urls to deliver their payloads:
19/09: iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @pr0xylife | Malware Bazaar | Tria.ge
20/09: url > .zip > .iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @pr0xylife | Malware Bazaar | Tria.ge
22/09: url > .zip > .iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @pr0xylife | Malware Bazaar | Tria.ge
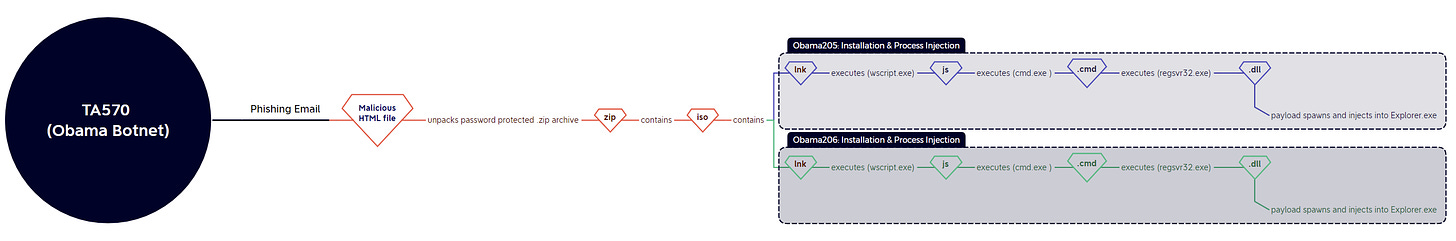
Obama Botnet
The Obama botnet (TA570) was relatively quiet and used a straightforward execution chain with little/no variance. Similar to TA577, it used .cmd files to obfuscate the dll invocation instead of the .bat files used last week:
19/09 (Obama205): html > .zip > .iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @pr0xylife | Malware Bazaar | Tria.ge
20/09 (Obama206): html > .zip > .iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @pr0xylife | Malware Bazaar | Tria.ge
The Other Guys
Agent Tesla
0xToxin started the week with their analysis of Agent Tesla samples used by the Aggah/Hagga actor. They found its PowerShell droppers pulling payloads from BitBucket and pushing exfil via authenticated FTP;
Another campaign identified the next day by 0xToxin saw AgentTesla being delivered through OneDrive links in Phishing emails, with exfil being performed via Telegram.
Another campaign from the 22nd sent Phishing emails with two archives attached. The first as a .r00 archive (RAR) that contained a .js file (vjw0rm/wshrat) that delivered the Agent Tesla payload . The second was a .gz archive that contained an exe that installed wshrat, followed by Agent Tesla. Exfil observed in this campaign was done via authenticated SMTP.
IcedID
A campaign observed on the 21st saw IcedID using thread hijacked emails to deliver password-protected zip files that contained ISO images. The execution chain from there was nearly identical to the BB and Obama Qakbot botnets - lnk > js > cmd > dll.
BumbleBee
@pr0xylife’s analysis of samples from the 19th showed the payload delivered via a zipped iso that used an lnk > bat > ps (net.webclient download) > dll (rundll32.exe) execution chain;
@kostastsale added to the above analysis, highlighting the follow-up enumeration activity and WMI queries used in addition to the standard nltest and net.exe LOLBIN activity that you can hunt for/detect on.