ESXiArgs - from bad to okay to bad again
Defenders breathed a sigh of relief as CISA this week released a recovery script to combat the growing infections of ESXi environments with the new ESXiArgs ransomware strain.
Ransomwhere - a group tracking ransom payments being made - found nearly 3,000 potential infections, and as of the 7th of February had identified at least 4 payments made, netting a nifty total of $88k revenue for the attackers.
Not bad for a low effort campaign, even if CISA did rain on their parade with the sharing of their recovery script.
Round 2
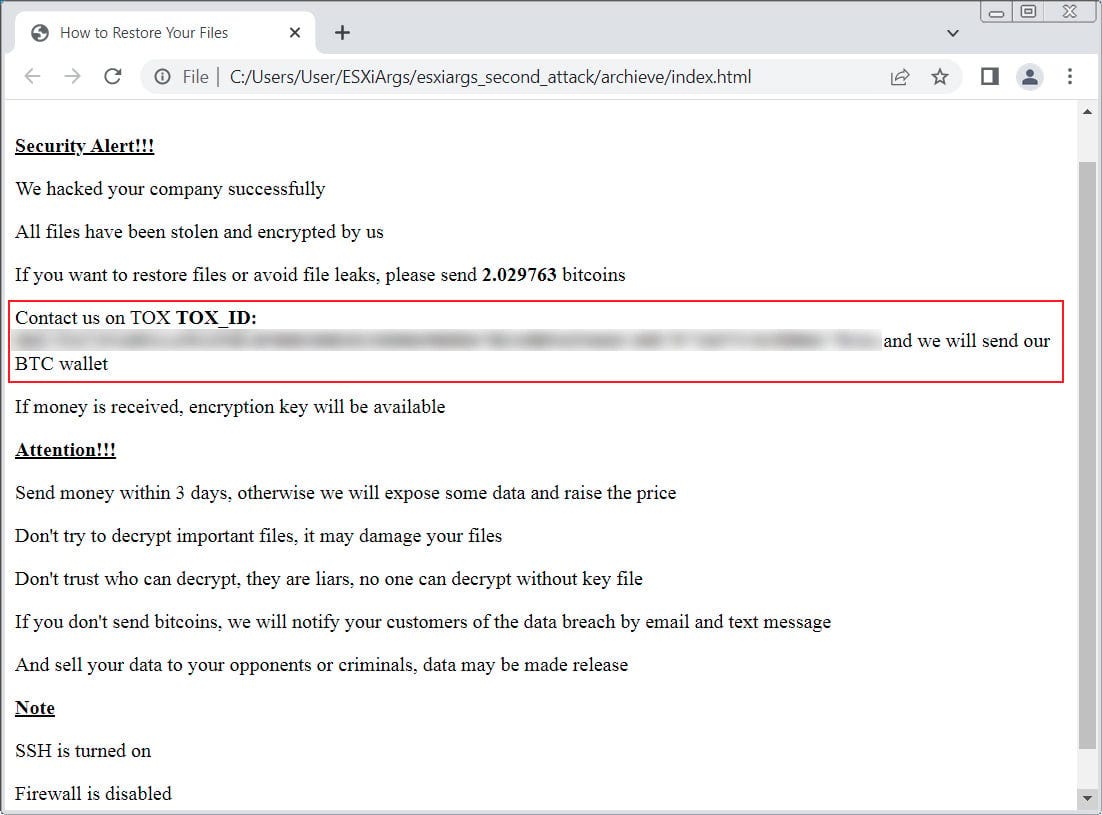
Unfortunately the attackers didn’t throw in their towel there, and - the very next day - initiated a second round of attacks that reinfected hosts with a revised strain which addressed the flaws in the encryption process - effectively nullifying CISA’s recovery script.
Thankfully, the number of hosts infected in the second wave appear to be much lower than the first, indicating that many organisations had taken steps to mitigate their vulnerable instances.

It also seems the attackers were paying attention to efforts by researchers such as Ransomwhere who were tracking the bitcoin wallets receiving payments, and had removed the wallet addresses in the second wave of attacks to prevent this.
What’s more concerning, though, is that some victims reported being reinfected despite disabling the OpenSLP service which was believed to be the cause of these compromises, and confirming the attacker’s vmtool.py backdoor wasn’t present.
Initial Access vector in dispute
These attacks were initially believed to be enabled through exploitation of CVE-2021-21974. This has been debunked, with other vulnerabilities in ESXi’s OpenSLP service also flagged as equally likely candidates.
Moreover, observers such as Censys has gone one step further in saying that OpenSLP “does not appear to be the method of attack, given that multiple compromised hosts did not have SLP running.”
What now?
Given the specific means of infection remains unknown, the best bet is to do what every organisation should have done from the start - remove your ESXi hosts from the internet!
Putting it behind a VPN and/or bastion host will still allow you to manage your ESXi environment remotely, while at the same time not exposing it to the internet for probing and exploitation by malicious actors.
For those looking to understand this campaign on a more technical level, TrustedSec have shared their analysis of the ESXiArgs ransomware, and while the means of intrusion in this article has since been proven incorrect, the remaining Indicators of Activity and recommendations may prove useful in constructing Hunts and Detections.
Infection chain for new malware loader shows shades of Qakbot, Matanbuchus
Early last week Unit42 reported on a OneNote infection chain which they believed at the time to be part of a Qakbot campaign, and delivered a 2nd-stage payload of Matanbuchus.





Despite the similarities, subsequent analysis by malware analyst German Fernandez showed it’s something else, which has since been dubbed “iPikaBot” based on unique strings in the HTML code of the C2 server.
Further research by cyber security company DCSO shows that while it does have technical similarities to Matanbuchus - it’s still unclear if they’re related, and if so, to what degree.
The malware looks to be in early development, and possesses rudimentary capabilities that allow the operator to run commands, fetch additional payloads, and configure the C2 check-in interval.
While its capabilities are a far cry from the more developed players such as Qakbot and Matanbuchus, the fact it is being distributed via a OneNote execution chain and appears to operate as a loader for additional malware make this a potential new malware family to look out for.
Other Reporting
🔥The DFIR Report have shared analysis of a very interesting intrusion by TA452 - a threat group which overlaps with Iran’s APT34/OilRig crew. The initial implant was fully implemented in PowerShell, dropping no executables and remaining fully undetected for a significant period of time. A keylogger was also built using Window’s AutoHotKey scripting language and executed through a renamed AutoHotKey.exe binary;
🔥DPRK actors have been leveraging both privately developed and publicly available tools and ransomware to generate revenue for the hermit kingdom, according to a new advisory published by CISA. Custom strains such as Maui and H0lyGh0st were flagged, as well as the well-known lockers of LockBit 2.0 and Ryuk;
Microsoft have published a report that looks into the MagicWeb backdoor that NOBELIUM (APT29) abused in attacks conducted around August last year. We noted at the time that MagicWeb was noteworthy for its abuse of ADFS procedures to provide attackers a stealthy means of re-entry to an environment should they be evicted;
🔥Rapid7 have examined the use of PlugX by China-based actors such as Mustang Panda, and shared a YARA rule that seeks to detect code patterns for PlugX’s dll component;
The Medusa Botnet - originally built on leaked Mirai source code as a DDoS botnet - now appears to have had ransomware capabilities and a Telnet brute-forcer bolted onto it. The ransomware feature unfortunately wipes system files too, preventing victims from being able to view the ransom note left behind - whoops!
SentinelOne have reported that CL0P ransomware’s Linux variant has been operating with flawed encryption routines for some months now, allowing them to publish a free decryptor and for victims to quietly recover their systems without paying ransom demands;
A Linux variant of Royal ransomware has been observed on VT, and looks to be built to target ESXi servers;
🔥Proofpoint have unveiled their latest threat group, TA866. This actor is noteworthy for their use of the 404 Traffic Distribution System to deliver targeted payloads; abuse of the Windows AutoHotKey scripting language, and for taking screenshots of target environments before deciding whether to progress further in the intrusion;
For anyone tracking TA580 - they’ve switched back to delivering BumbleBee loader instead of Cobalt Strike in this week’s campaign, and notably are one of the few still using the ZIP > IMG > LNK delivery chain at the moment;
0xToxin has shared a detailed write-up of their analysis of an ASyncRAT OneNote campaign;
🔥Bookmark this, a handy config extraction script for the latest ASyncRAT payloads;
🔥Kostas Tsale has this neat wrap-up of behaviours exhibited in recent ASyncRAT delivery campaigns, as well as a few tips on how to hunt or detect for this activity;
If you’re still getting to grips with OneNote execution chains, this thread provides a nice summary of the distinct stages and anomalous behaviours you can detect on;
This post from Trellix looks at the recent uptick in SEO-Poisoning through the lens of a well-known adopter of the technique - GootKit;
Expel Security have shared their annual trends report, noting the prevalence of BEC - comprising 50% of attacks - and a shift away from abusing legacy protocols to bypass MFA in m365 in favour of Attacker-in-the-Middle (e.g. evilginx) techniques;
Spamhaus and Abuse.ch have shared their latest joint report looking at malware submissions, URLs and IOCs in January this year. RedLine and SmokeLoader were by far the most prominent threats in terms of URLs and samples submitted to URLHaus and Malware Bazaar respectively, while IOCs for Vidar, Mirai and Cobalt Strike took top spots on ThreatFox;
Emergency patch released for GoAnywhere MFT
An actively exploited 0-day vulnerability in Fortra’s GoAnywhere MFT software has finally received a patch, which was rushed out after nearly 1,000 instances were observed exposed to the internet and a PoC exploit was released last week.
While Fortra have opted against sharing any details beyond stating it’s being actively exploited, the operators of Clop ransomware (TA505) claimed to have leveraged it to steal data from over 130 organisations.
A separate post by Huntress Labs somewhat corroborates this, as they observed TrueBot - a malware family known to be used by TA505 - being deployed in an intrusion which appeared to stem from a compromised GoAnywhere MFT appliance.
8 Vulnerabilities in File Transfer appliances…and 0 patches
Security firm Rapid7 has publicly shared a list of eight vulnerabilities identified in several File Transfer appliances, which are still not patched more than two months after disclosing them to vendors.
The vulnerabilities all stem from XSS, and could potentially be abused to steal session cookies to create privileged accounts, or perform command injection in the context of the impacted user.
Offensive
🔥BokuLoader - A User-Defined Cobalt Strike Reflective Loader written in Assembly & C for advanced evasion capabilities;
🔥LocalPotato - Yet another Potato PrivEsc method, this time enabling a local escalation to System;
Offensive Docker - A docker container with many core offensive tools to help you get up and running quickly;
TrustedSec have released a new version of TeamFiltration - their attack framework for targeting Office 365 Azure AD accounts. It comes with a few significant upgrades, including integration with FireProx, allowing you to cycle through source IPs while running the tool;
Another one from TrustedSec, this time looking at pivoting from a compromised AD environment up to the cloud;
QuarksLab have published a write-up on the potential to leverage a malicious plugin to achieve code injection in KeePass instances, accessing memory and dumping all stored passwords at runtime;
A topical write-up that will be useful for both Red and Purple teamers - a guide to creating OneNote phishing lures;
This diagram might prove a handy reference on your next engagement, as it maps out the various ways an attacker can attempt to Bypass AV/EDR solutions - making direct syscalls, employing packers, disabling ETW, and more.
Defensive
FQDN Parser - a tool to help extract FQDN components, adding useful metadata such as date of registration, the TLD type (e.g. .onion), and more;
Secrets Patterns Database - A cache of over 1,600 regular expressions to help you sweep for secrets, passwords, tokens, and more;
Check out Part 2 in this series on Linux’s auditd - this time looking at how to read the generated events in the context of threat hunting;
🔥Splunk’s Threat Research Team have published a fantastic guide to hunting for IIS backdoors, paired with handy set of queries to help you on your way;
SpecterOps’s article on Telemetry Layering is a good call-out that it’s important to identify, understand, and utilise a variety of sources in order to create flexible Detections;
🔥Elastic have shared an overview of several detections written in EQL that alerts on a series of common dll abuse methods. The underlying logic makes for a great starting point for teams looking to detect this frequently seen attack medium;
This thread by @snovvcrash is a handy illustration of the challenges facing Detection Engineers - stripping out unnecessary requests and manually assigning values in a DCSync attack allows for it to bypass IDS rules that are built expecting the full flow to take place;
Olaf Hartong from FalconForce has shared the latest installment of their series looking at Microsoft Defender for Endpoint, this time evaluating it how its Timeline function stacks up against the tried and true Advanced Hunting solution.
Cyber security firm Ke-La have shared a report looking at Telegram’s role in the Dark Web Marketplace, enabling the pedaling of stolen data; sale of capability such as infostealers, and recruiting for ransomware crews;
eCommerce security vendor Sansec has found ~12% of online stores they surveyed were inadvertently exposing their site backups, potentially resulting in leaks of sensitive back-end credentials and customer data;
Something for security architects to carefully consider - cloud security company Permiso have found in 2022 that Cloud Apps only utilised 11% of permissions granted - not much better than the 2~5% figure in a study performed two years prior.
A little something to congratulate you on making it to the end of the newsletter - vx-underground’s meme game has always been on point!