A swing and a miss at Genesis Marketplace - or was it?
A cabal of Law enforcement agencies teamed up to take down the clear-web sites for Genesis marketplace earlier last week, a cyber criminal marketplace in operation since 2017 which traded in credentials, cookies, and device fingerprints which could be used to impersonate victims and even bypass MFA protections.
The marketplace is one of the most successful Initial Access Brokers in operation today, and if you haven’t heard of them - that breach of EA back in June 2021? That all started with a set of credentials bought on this marketplace, for a paltry $10.
A statement issued by Europol noted that the takedowns - performed under the aptly named “Operation Cookie Monster” - coincided with “119 arrests, 208 property searches and 97 knock and talk measures” performed across the globe.
The Head of Europol’s European Cybercrime Centre, Edvardas Šileris, celebrated their victory by proclaiming they had “severely disrupted the criminal cyber ecosystem by removing one of its key enablers.”
Close, but not quite
Unfortunately, Edvardas’ celebrations appeared to be premature as, according to cyber security company ZeroFox, “the site remains accessible, stable, and functional via the TOR address”, and new and updated inventory continued to be listed on the Genesis marketplace following the alleged takedown.
The most tangible impact appeared to have been that operation of the Genesis Marketplace browser plugin - which allowed users to impersonate the purchased identities of their victims - relied on the clear-web infrastructure to operate. Soon after the takedown, the admins acknowledged the impact and that they were working to launch it on TOR as a workaround.

59k users in the crosshairs
While the admins may have gotten away unscathed - for now - the FBI claimed to have gained access to the back-end servers running the marketplace which enabled them to siphon records for approximately 59,000 user accounts. The dataset included their usernames, passwords, email accounts, secure messenger accounts and user history.
These records are what helped investigators determine the true identities of users on the marketplace, and to subsequently make their arrests. With just 119 arrests made so far, it’s likely there’s more yet to come.
As we mentioned the other week - if you take down a marketplace another will emerge eventually, but if you degrade the very trust that underpins the ecosystem itself? Well, actors will have a hard time figuring out who’s friend or foe; which platforms are run or backdoored by law enforcement agencies, and struggle to build the criminal partnerships which have proved vital in enabling the production-line of cyber crime.
With the demise of Breached Forums still fresh in recent memory, cyber criminals are likely to be feeling the ground shrink beneath their feet. This is exactly what law enforcement agencies will be hoping for; is key to disrupting the cyber criminal ecosystem, and needs to continue at-pace to be effective.
Crackdown on Cobalt Strike cracks
Confusing headline, I know. ¯\_(ツ)_/¯
Microsoft has announced it’s kicking off a concerted effort to stamp out abuse of cracked versions of the offensive Cobalt Strike framework, in partnership with the Health ISAC and Fortra - the vendor for Cobalt Strike.
The highly capable and ubiquitous hacking tool - while sold and intended for legitimate use in approved Red Team and Penetration Testing activities - has long been abused by APT groups and cyber criminals alike, who have consistently leveraged it in countless real-world attacks.
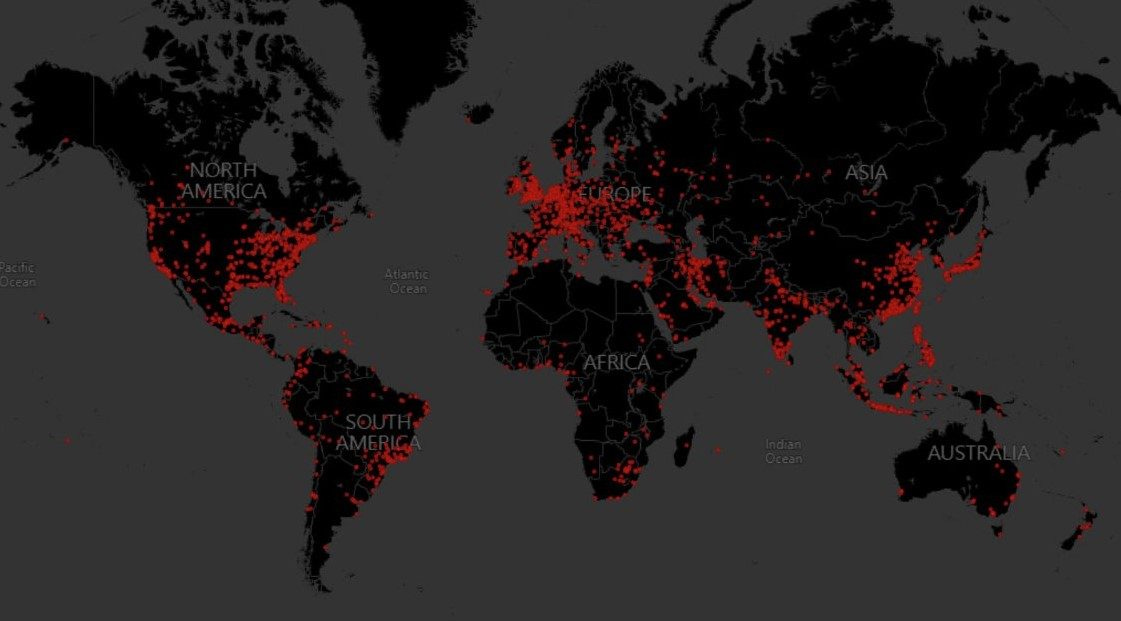
While this initiative is welcome in that it will almost exclusively be targeting abuse of the tool for malicious purposes, the scale of the challenge before them is clear when looking at the above map.
Originally released in 2012, Cobalt Strike has been the offensive tool of choice for over a decade. In that time it’s come to be distributed throughout networks across the world, and despite increased experimentation with alternate offensive frameworks (e.g. Sliver, Mythic, and Covenant in the below image), Cobalt Strike remains entrenched in the toolkits of malicious actors.
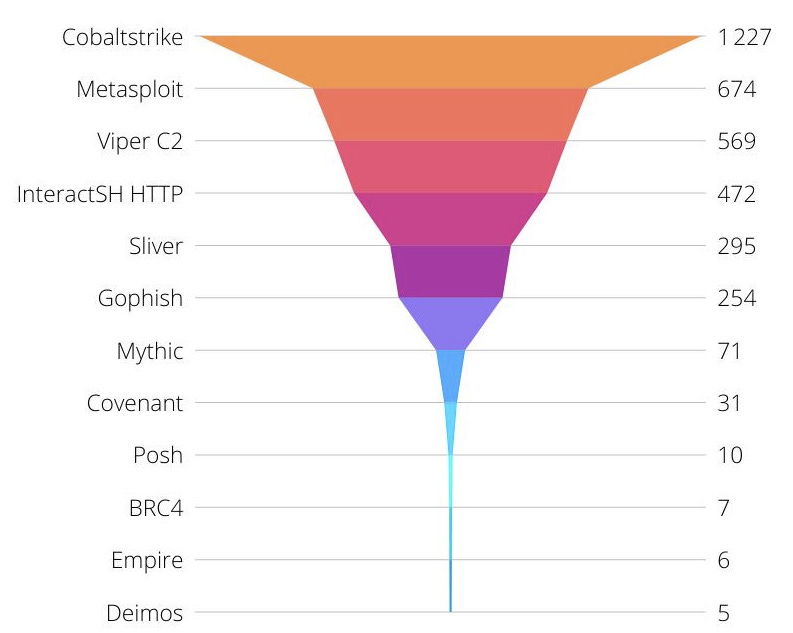
In the first instance, it’s likely cyber criminals will continue spinning up infrastructure with a few tweaks or through different bulletproof hosting providers to see if Microsoft can keep up with their changes. If not, this initiative is unlikely to get much traction.
Moreover, the consortium will be reliant on international CERTs and ISPs to cooperate in taking down the infrastructure, which will potentially delay takedown attempts or hit a dead-end where international ISPs simply don’t comply.
Challenges aside, given the scale of abuse of this tool and the real-world impact it’s had - this is a worthwhile endeavour, and touch wood we’ll see some runs chalked up in the coming months.
Other Reporting
Researchers from Kaspersky have uncovered what they believe to be the final payload delivered in the 3CX supply-chain attack from last week - a 3-year old DPRK backdoor dubbed “Gopuram”, which they’ve only observed delivered with “surgical precision” to a select few targets;
Mandiant have reported observing the ALPHV ransomware gang leveraging a trio of vulnerabilities in the Veritas Backup software to gain access to victim networks. A Metasploit module was created for the vulnerability in September last year, making it trivial to exploit, and earning it a spot on CISA’s KEV;
Google’s TAG have followed up on Mandiant’s promotion of APT43 - attributed to North Korea's main foreign intelligence service, the Reconnaissance General Bureau (RGB), with their own overview of the actor which overlaps with an actor they track as ARCHIPELAGO;
🔥Microsoft have published a report analysing a campaign involving an Iranian nation-state actor tracked as MERCURY collaborating with another actor - DEV-1084 - to conduct a protracted compromise of a victim’s on-prem and cloud environments, which culminated in a composite ransomware, data exfil, and destructive attack;
The DFIR Report has released their latest write-up on an intrusion, this time reviewing an IcedID > Quantum ransomware case from September last year that took the attackers just over 78 hours;
Researchers from Sucuri have highlighted a five-year campaign which has compromised approximately one million WordPress websites with the Balada Injector malware. The attacks comprising this campaign come in waves and leverage refreshed infrastructure each time, with the end goal of redirecting visitors to fake tech support pages and other scam websites;
Cisco Talos have a new report looking at the revamped Typhon Reborn infostealer - with improved anti-analysis and evasive measures and multiple purchases observed on the Dark Web, Talos warns it’s a potential upcoming threat to be on alert for;
Intel firm Cyfirma report that channels operated by the ARES Group have increased in activity with the shutdown of Breached Forums, and is shaping up as a trusted broker for stolen PII and services such as malware development, DDoS attacks, and more;
Resecurity has also picked a candidate for Breached Forums successor, pointing to the newly minted STYX forum which - despite only going live in January this year - already has an established escrow service to facilitate trading in PII, tooling, and services including money laundering, document forgery, and more;
The 2022 wrap-up of threats to the Energy sector is a very handy reference indeed - thanks to the analysts at Sekoia for such a detailed, and yet succinct report!
PwC have also finally released their 2022 retrospective, which comes with a neat break-out of threats observed by sector throughout the year;
🔥Sysdig have shared an interesting article which explores proxyjacking - a relatively new monetisation avenue for cyber criminals, involving dropping legitimate proxyware applications on compromised devices and on-selling that access to traffic proxying service providers such as IPRoyal, HoneyGain, and more.
PoC released for CVSS 10.0 Sandbox Escape vulnerability
Two versions of PoC code have been released publicly which exploit CVE-2023-29017, a vulnerability which would allow an attacker to escape the VM2 JavaScript sandbox and gain code execution on the underlying host.
Versions 3.9.14 and earlier are impacted by the vulnerability - no workaround exist other than to upgrade to the patched version 3.9.15.
With over 16 million monthly downloads of the package from npm alone, this is one to keep an eye out for as it’s highly likely some projects which rely on this dependency will either miss or delay updating the package, and remain vulnerable for some time.
HiSilicon, Qualcomm-powered WiFi vulnerable to ICMP attack
Researchers have tested 55 WiFi Access Point (AP) products from 10 vendors that used either HiSilicon or Qualcomm chips, and found that all were vulnerable to an ICMP vulnerability which allowed them to intercept and snoop on the traffic of other connected clients.
The flaw (CVE-2022-25667) works against WPA, WPA2, and WPA3 networks, and stems from an attacker sending an ICMP redirect message to the target which is spoofed to appear as though it originated from the AP.
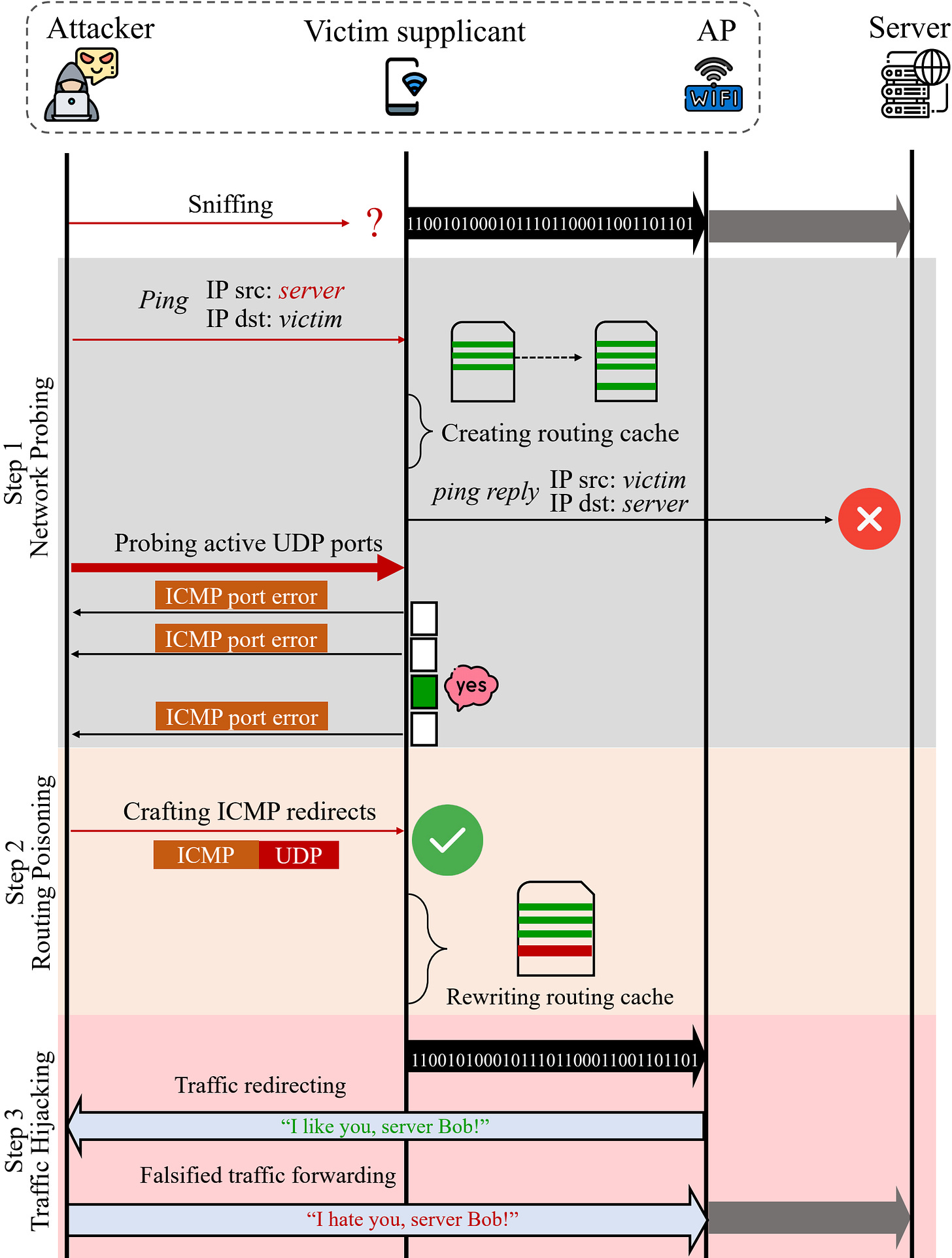
While you’d think the AP would discard messages that spoof itself as the origin, it’s due to performance limitations within the Network Processing Unit (NPU) itself that it instead simply forwards it on.
The researchers also noted that ACL’s are an ineffective mitigation against this attack as the forged messages are transmitted at a lower level of the network stack - i.e. before those rules kick in.
Other Vulnerabilities
Apple patch 0-day vulns in mobile, laptop platforms
Apple has patched two new 0-day vulnerabilities on Friday, both of which they claim to have observed exploited in the wild.
The first vulnerability - CVE-2023-28206 - can be abused through delivering a maliciously crafted app which can exploit the flaw in the IOSurfaceAccelerator to achieve kernel-level code execution on target devices.
The second is CVE-2023-28205, which can enable data corruption or code execution through simply tricking a target into loading a malicious web page.
CISA pile on warning of Zimbra exploitation by Russian actors
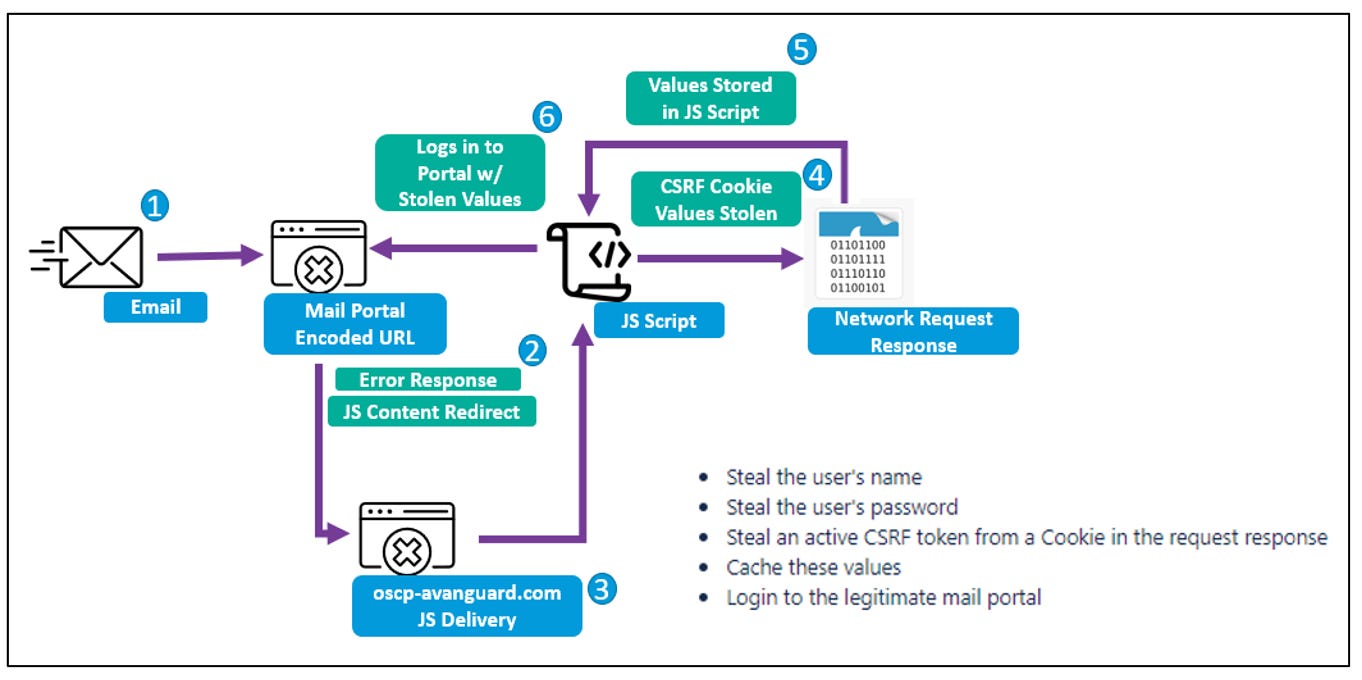
CISA have added CVE-2022-27926 to the Known Exploited Vulnerabilities list following a report last week by Proofpoint that highlighted the Russia-affiliated TA473/Winter Vivern APT was leveraging it in attacks on NATO-aligned governments.
The Cross-Site Scripting (XSS) vulnerability in the Zimbra Collaboration suite was being abused to “steal usernames, passwords, and store active session and CSRF tokens from cookies”, enabling them to access the email mailboxes of “military, government, and diplomatic organizations across Europe involved in the Russia Ukrainian War.”
Offensive
🔥MFASweep - A PowerShell script that attempts to log in to various Microsoft services using a provided set of credentials to identify if MFA is enabled;
Two repositories to help testing for argument injection opportunities - GTFOArgs, and a similar project by SonarSource;
🔥TrustedSec have a neat write-up on a Tool Command Language (TcL) Script that will turn a Cisco router into a port-forwarding proxy to enable onward exploitation & C2;
The head of research at Wiz has shared a follow-up thread that walks through how they scanned and enumerated exposed Azure App Service and Azure Functions en masse to uncover the BingBang attack path they reported on last week.
Defensive
🔥CA Optics - an Azure AD Conditional Access Gap Analyzer, to help make sure you find and patch any cracks in your policy;
🔥LOLDrivers.io - a curated list of Windows drivers used by adversaries to bypass security controls and carry out attacks, with the catalogue set to expand to include vulnerable, malicious, and experimental drivers, as well as compromised certificates;
Speaking of drivers, Eric Capuano of Recon Infosec has shared a tidy list of resources to help understand and mitigate against the rising abuse of the Bring Your Own Vulnerable Driver (BYOVD) technique;
Michael Koczwara has some great hunting tips for discovering C2 infrastructure that’s been spun up with default certificate names for the Sliver and Havoc frameworks;
🔥Crowdstrike have put together an interesting article looking at self-extracting archives (SFX archives), highlighting how they can be abused to enable SYSTEM-level persistence by threat actors;
Malware researcher @embee_research has shared a post dissecting a DCRat sample, stripping back layers of obfuscation with CyberChef to unpack the final payload;
0xToxin has taken a look at a LummaC2 stealer sample, providing a comprehensive walkthrough of the multiple stages of obfuscation employed by the malware and demonstrating how to dump a list of malicious Chrome Extensions the tool masquerades as;
🔥Microsoft have updated the Preview version of Microsoft 365 Defender advanced hunting with the ability to search and correlate results based on defined “Behaviours” such as multiple VM creation activities, mass download, or suspicious PowerBI report sharing. The idea is to pull these low-fidelity detections out of the alerting queue, while keeping them available in a schema for correlation during investigations;
Alex Teixeira has been on a tear these last few weeks, this time putting out a post exploring the use and misuse of SOAR platforms in Detection Engineering;
Airwalk Consulting have shared a neat post and diagram which maps a potential Threat Model for the AWS Key Management Service (KMS);
🔥Attacks on CI/CD DevOps pipelines aren’t a widely or deeply understood concept within infosec, so it’s well worth having a read through Microsoft’s take on an ATT&CK-like Threat Matrix for exactly that.
Make sure you’ve got your ducks in a row - Windows 10 v21H2 is hitting end-of-service (EOS) on June 13, Exchange and SharePoint Server 2013 are going EOS this week - if your org hasn’t got migration plans in motion yet, this thread has links to useful resources to help with that;
The UK’s Criminal Records Office has finally copped to a breach after insisting for weeks that it was simply performing “essential website maintenance”. The compromise was discovered on March 21st, but may have begun as early as January 17.