Headline Items
The growing professionalisation of cyber crime - the Genesis Marketplace & Dark Utilities C2 service enable force amplification from initial access to payload delivery & C2;
SentinelOne take a look at growing adoption of lnk files during payload execution, examining common lnk execution chains & highlighting detection opportunities for defenders;
RCE vulnerabilities galore in VMWare, Cisco, and DrayTek devices & software.
Emerging Tooling & Services in the Dark Web Marketplace
Reference: Sophos X-Ops | Cisco Talos | Cisco Talos
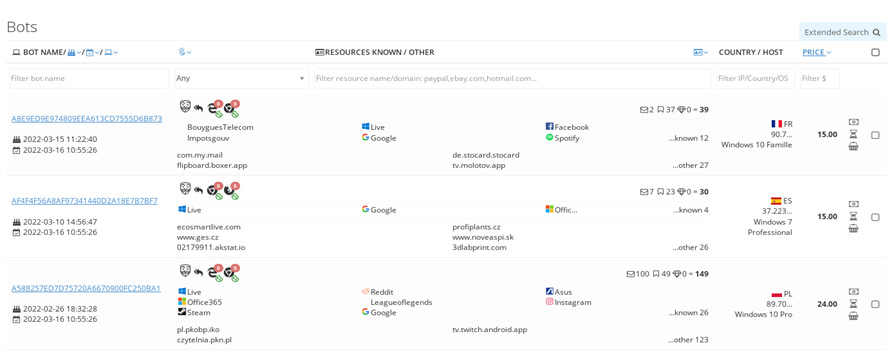
Sophos have released a detailed report on Genesis Marketplace, a popular and highly-regarded dark web front that sells IAB services - stolen credentials, cookies, and endpoint “fingerprints” are up for grabs, as well as the tools needed to use them. Notably, they claim that as long as they maintain access to the compromised system, the victim data will continue to be updated for the purchaser to use.
Genesis is a polished, invite-only operation with a wiki and FAQ available and multilingual tech support. The user dashboard shows which of their purchased “bots” (compromised systems) have been updated since their last visit, with data easily searchable for prospective customers.
Cisco Talos has reported on a new ‘C2-as-a-Service’ offering called Dark Utilities that’s been gaining traction on the dark web, claiming to provide anonymised infrastructure on both Tor and the clear web for as little as EUR 9.99. In addition to enabling DoS and Cryptojacking attacks, the service provides a point-and-click payload generator that supports multiple OS variants, and hosts attacker payloads using the decentralised Interplanetary File System (IPFS) - something we covered last week as observed in Phishing campaigns by Trustwave.
Another finding by Cisco Talos was Manjusaka, an attack framework advertised as an imitation of Cobalt Strike and seen deployed in a handful of attacks, seemingly to test its efficacy. The implants are written in Rust - which will complicate attempts to reverse it - and provides basic enumeration, code execution and information stealing capabilities. Given the tentative trend of attackers looking to move away from Cobalt Strike (e.g. using Brute Ratel, Sliver), even a moderately capable alternative could gain traction - given the right price point and roadmap for development.
IABs are an integral component in the cyber crime ecosystem and directly enable the conduct of ransomware operations. It’s worth keeping track of where they sell their accesses to see if access to you, a partner or a vendor may be up for grabs.
Cyber crime actors - especially those that operate at-scale - will find value in a full-featured offering like Dark Utilities that automates C2 and payload generation, and will likely continue to gain traction and adoption as word spreads.
While Sliver and Metasploit have been the primary alternative to the Cobalt Strike attack framework, one of their main weaknesses is that they’re freely available and therefore open to reversing and detection engineering by defenders. This means less-known, pay-walled offerings like Brute Ratel may present as more attractive alternatives - as may the newly-minted Manjusaka framework, in time.
Spotlight on LNK abuse patterns
Reference: SentinelOne
While last week’s commentary on the shift away from Macros focused largely on the delivery of container files (iso, rar, zip, etc.), a report from SentinelOne has looked specifically at trends in how the subsequently unpacked lnk files are used to execute attacker payloads.
High-level points:
The research looked at 27,510 malicious lnk files from VirusTotal between June 14, 2021 to the same time this year. 68.89% of the samples were submitted in 2022, highlighting the significant increase in utilisation from the end of last year;
95% of attacks analysed launched cmd.exe from the lnk file. From there, some (15.195%) used LOLBINs to execute the final payload:
explorer.exe, powershell.exe and wscript.exe were the most commonly seen LOLBINs used to invoke attacker payloads;
99.914% of .exe payloads were dropped with random, high-entropy names and run through cmd.exe;
Over 253 non-exe extensions were abused, typically other executable file extensions (scr, dll), data files (log, dat) or script file types (vbs, js). These often masqueraded as other file formats like media files, and were also run through cmd.exe
The report also touched on mLNK and QuantumBuilder, two actively developed and prominent lnk weaponising tools available on the dark web. They’re both relatively affordable and provide attackers the ability to automate generation of obfuscated and weaponised lnk files, complete with evasion and AV bypass measures baked in.
Zimbra Collaboration exploited in-the-wild
Reference: Bleeping Computer
Addressed with the release of patches in May this year, CVE-2022-27824, has been added by CISA to their Known Exploited Vulnerabilities Catalogue, signalling that in-the-wild attacks have been observed some two months after initially being reported.
The vulnerability is present in Zimbra Collaboration and would allow an unauthenticated attacker to steal email account credentials in cleartext form.
The obvious theft of email aside, this could enable onwards malspam delivery to facilitate BEC, Phishing, and other social engineering-type attacks on contacts of the compromised account.
Critical RCE vulnerabilities in Cisco & Draytek devices
References: Bleeping Computer | Hacker News
Two vulnerabilities in Cisco’s Small Business VPN routers, CVE-2022-20841 and CVE-2022-20827, would allow unauthenticated RCE as root or DoS attacks on vulnerable devices if exploited. Check the list of impacted devices here.
Not to be outdone, multiple variants of DrayTek’s “Vigor” routers are vulnerable to a CVSS 10.0 flaw that allows for unauthenticated RCE in the management interface. Trellix, who discovered the vulnerability, said there were some 200,000 instances with this exposed to the internet (yikes) at the time, and for those that aren’t - this can still be exploited as a one-click vulnerability from within the LAN. Patches are here.
CVSS 9.8 RCE in multiple VMWare products
Reference: El Reg
CVE-2022-31656 is a critical vulnerability in VMware's Workspace ONE Access, Identity Manager, and vRealize Automation products. Successful exploitation would provide attackers with admin access without needing to authenticate - but they do need network access to the UI to do so. There are no known instances of in-the-wild exploitation or exploit code.
While it goes without saying that this should be patched ASAP, this vulnerability was one of nine addressed by VMWare and includes several other RCE and Privilege Escalation vulnerabilities that affect the same suite of products, so make sure you jump on those while you’re at it!
Offensive
The Bloodhound project got a major facelift - key points:
Bloodhound 4.2 release is out;
An additional tool, the BloodHound Attack Research Kit (BARK) has been released to assist with validating abuse primitives;
Andy Robbins has provided a neat example of how the improved AzureHound can be used with BARK to test an escalation path to Global Admin, including highlighting what you need to do to mitigate against it in the Prevention section of this post.
A detailed write-up on automating tool obfuscation using Jenkins;
RedGuard, an open-source C2 Flow Control framework aimed at evading “Blue Team, AVS, EDR, Cyberspace Search Engine.”
Defensive
Monkey365, a tool to help review Microsoft 365, Azure subscriptions and Azure Active Directory for security misconfigurations;
PersistenceSniper, a PowerShell tool that will hunt for 31 persistence methods - handy for incident responders to add to their portable toolkit;
Performing IR on GCP? Here’s a cheat sheet of potentially abused APIs to inspect your logs for;
A thread from Stephan Berger on hunting for ASyncRAT C2, persistence, and use of mutexes;
Another quality, in-depth blog post from Lina Lau (@inversecos) on detecting time-stomping in Linux filesystems;
VirusTotal have added Threat Actor Collections to the platform - a logical way to search for samples and a welcome addition;
Elastic have shared over 1000 YARA rules and 200 endpoint behaviour rules to make life easier for you.
Unit 42’s analysis of the BumbleBee loader used by EXOTICLILY, believed to be an IAB for Conti, whose affiliates have reportedly since splintered to work with various highly capable ransomware operations;
The popular RaccoonStealer, sold on the dark web, got a v2 release in July, and zScaler have this detailed technical analysis to share with us. A few operations like RIG ExploitKit ditched it when the original developer was reportedly killed in the Russian invasion of Ukraine in June this year, so time will tell if it regains its fan base;
Gootkit, often used by downstream actors to obtain initial access through SEO-hijacking search results for free software, have switched to using real estate-themed legal documents as lures;
A Qualys report on QuasarRAT - an open source RAT used by multiple threat groups, though notably including the Chinese actor APT10;
The ACSC and CISA have produced a joint advisory on the most prevalent malware strains seen in 2021. Congrats to Qakbot and Ursnif for taking out the old-timers award with over 10 years in the running. Now please leave.