This is an extended newsletter, so it may be truncated towards the end of the email. To read the full post, just select the View entire message hyperlink at the bottom of the email or Open in Browser!
Google Play not the safe haven you might think
Kaspersky have published an article that examines trade on the Dark Web for services that deliver Android malware via legitimate apps on Google Play.
As an example, one ad for a Google Play Loader claims it can inject malware into legitimate apps such as cryptocurrency trackers, financial apps, QR-code scanners and even dating apps. The sellers also provide guarantees that the infected app will stay up for at least a week, or to target apps with at least 5,000 downloads in order to ensure the buyer can achieve a meaningful scope of compromise.
It turns out this side of the cyber criminal market is quite well developed, with the researchers additionally finding:
Attackers can also purchase Google Ads to increase downloads of the injected app, with ads for users in the US & Australia fetching the highest price of 80 cents per ad;
These Loaders can sell for as little as $2,000, or fetch up to $20k for the loader code itself;
Legitimate Google Play developer accounts can be purchased for as little as $60, depending on the reputation of the account and number of app downloads achieved.
A report released this week by McAfee examined the distribution of the Goldoson data-stealing and ad-clicking Android malware, which successfully trojanised 60 legitimate Google Play apps with a collective 100 million downloads, through a compromised 3rd-party library.
Nokoyawa Ransomware 0-day patched
Operators of the Nokoyawa ransomware family were observed deploying the CVE-2023-28252 zero-day as part of an active campaign, prior to it being patched this Patch Tuesday.
Kaspersky researchers noted the exploit for the vulnerability in the Common Log File System (CLFS) driver was likely developed by a single exploit author, who seems to have worked closely with the ransomware group in historical attacks.
The author is believed to have crafted five different CLFS exploits that were deployed in attacks on various industry verticals, conducted since at least June 2022.
Analysis of the ransomware payload itself also revealed that the developers were advancing in more ways than one, having deviated from simply using a fork of the JSWorm ransomware and instead appearing to have written a significantly distinct crypter for use in this attack.
Other Reporting
A report published from a joint investigation between Microsoft and Citizen Lab has uncovered the use of a mobile exploitation framework called REIGN, sold by an Israel-based Private Sector Offensive Actor (PSOA) known as QuaDream, and tracked by Microsoft as DEV-0196. Their tooling has been used to prosecute journalists, political opposition figures and NGOs, with their operators believed to originate from countries including the UAE, Ghana, Singapore, and more;
Kaspersky have shared a succinct synopsis of the North Korean “Operation DreamJob” campaign which spanned from late 2019 and to 2022 and targeted a range of industry verticals;
🔥IBM’s X-Force have found an apparent collaboration between members of the Conti Syndicate (FIN12/Wizard Spider) and FIN7, who appear to have joined forces to create the new Domino backdoor which has been used in-the-wild since at least late February this year;
Vice Society have taken living off the land to another level with a sophisticated PowerShell script employed in a recent campaign to perform data exfiltration. The script used generic cmdlets in order to blend in, and demonstrated a professional level of script coding in their implementation of a rate-limiting function to ensure it didn’t hog too much resources when running;
🔥Researchers at NTT have published their analysis of a campaign they’ve observed which repurposes compromised sites to dupe visitors into applying a fake Google Chrome update. Malicious scripts are delivered using the takedown-resistant InterPlanetary File System (IPFS), which ultimately drop a Monero miner that itself leverages the BYOVD technique to elevate its privileges to SYSTEM. It’s noteworthy that the two techniques - both of which are quite new - have been adopted by a simple crypto-mining operation;
Sekoia have shared a particularly interesting report which looks at the Initial Access brokerage scene and the myriad of techniques and services provided to facilitate delivery of malicious payloads;
Cado Labs report on Legion, a Python-based credential dumper being sold via Telegram which targets unsecured web servers running CMS software and PHP-based frameworks, hunting for and dumping credentials which it then uses to send spam or phishing emails, or even SMS spam through supported carriers;
Microsoft have published guidance to help investigate and detect exploitation attempts of CVE-2022-21894 in the UEFI bootkit, a la the BlackLotus bootkit;
Dutch Police are continuing to mess with former RaidForums members by sending the emails asking them to delete stolen data and stop performing illegal cyber activities, warning them that they are “less anonymous online than [they] think”;
KELA have published their latest report on ransomware trends, noting an increase for FY23Q1.
QueueJumper Vulnerability tops Patch Tuesday
The most noteworthy bug from this month’s Patch Tuesday fiesta was CVE-2023-21554, a vulnerability in the Windows Message Queuing (MSMQ) Service which could enable remote code execution through a low-complexity attack.
With over 360,000 MSMQ servers exposed to the internet and “past instances of this type of vulnerability being exploited” being noted by Microsoft, it’s no surprise it’s earned the rating of “exploitation more likely.”
Surprise, you’re vulnerable!
Checkpoint, who reported the bug, have also noted that if an administrator checks the “Automatically install Windows Server roles and features that are required to install Exchange” option - as recommended by Microsoft - the MSMQ service will be installed and enabled in the background:

Moreover, some have reported that the service remains active even after uninstalling the software that this was packaged with - not something the ordinary admin would think they’d need to check for as part of the uninstall process.
Exploitation Imminent
While no exploit PoCs have been made public and there’s no evidence of exploitation as of yet, the fact that this can be exploited remotely; paired with the sheer volume of exposed endpoints mean it’s likely we’ll see exploitation in the coming days and weeks.
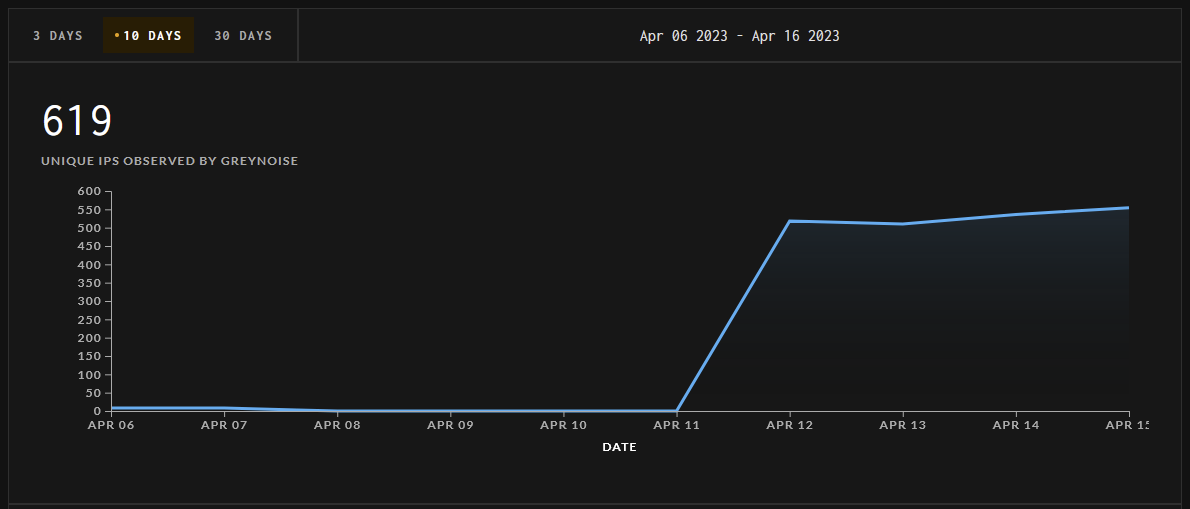
The precursors are already there - Greynoise are tracking IPs scanning for internet-connected MSMQ endpoints, and have observed a steady volume of activity since the vulnerability was reported last week:
The bottom line - make sure you expedite your patching or at least pull any exposed endpoints you might have behind a firewall - before it’s too late.
Unpatched Intune vuln could lead to user impersonation
Microsoft have opted not to fix a vulnerability identified in their Mobile Device Management platform Intune, after sitting on the bug for nine months.
Offensive Security shop BishopFox reported the flaw back in July 2022, which stemmed from the Microsoft Intune Management Extension failing to properly enclose the path to its agentexecutor.exe utility in quotation marks.
Per their advisory: “An attacker with write access to the root of the C:\ drive or the C:\Program Files (x86) directory could execute code in the context of another user by creating a malicious executable named C:\Program.exe or C:\Program Files (x86)\Microsoft.exe, and then wait for Intune to call the agentexecutor.exe utility program.”
While the vulnerability could be exploited for vertical or horizontal privilege escalation, it requires the attacker to have local administrator privileges in order to write files to the affected locations.
Azure Shared Key Authorisation a potential lateral movement risk
Researchers at Orca Security have highlighted an attack path that leverages the permissions of a compromised account with the Storage Account Contributor role to identify and backdoor the code hosted in storage accounts - which are created as part of the process of deploying a Function App.
The attacker could then go on to hijack the access token for the managed identity associated with the account, effectively elevating their privileges in a way that doesn’t present in the Azure Activity Log.
Microsoft don’t view this as a vulnerability, but an abuse of intentional functionality. They’ve released a Best Practices guide for how to manage storage account privileges and detect potential abuse.
This one may be best left to your Red Team to validate your org’s exposure, and ensure your implementation of least-privilege is up to scratch.
Other vulnerabilities
SAP patch 24 bugs - two critical
Software vendor SAP has published fixes for 24 bugs, with two critical bugs among the mix.
The most severe of the two is CVE-2023-28765, which comes in with an eye-watering CVSS score of 9.8. The information disclosure vulnerability would allow an attacker with basic privileges to obtain the credentials of the platform’s users;
CVE-2023-27267 stems from insufficient input validation and missing authentication controls, which could result in code execution on deployed SAP Diagnostics agents.
Offensive
🔥SharpHound4Cobalt - A Cobalt Strike port of the BloodHound collector that will enable in-memory collection & communication of BloodHound recon data;
BurpGPT - A Burp Suite extension that integrates OpenAI's GPT to perform an additional passive scan for discovering highly bespoke vulnerabilities, and enables running traffic-based analysis of any type.
Seekr - an OSINT tool with a neat GUI and helpful note-taking features to aid in tracking complex cases;
QuadraInspect - An Android framework that integrates AndroPass, APKUtil, RMS and MobFS, providing a powerful tool for analyzing the security of Android applications.
🔥TrustedSec have kept the gems flowing this week with this article on how to leverage stolen Office tokens to bypass MFA and access cloud workloads;
🔥Security researcher @nas_bench has found a list of suspicious keywords that Microsoft looks for in PowerShell activity to determine if it’ll generate a 4104 event log - regardless of the configured logging policy. It’s good trivia for the blue team, but a great Opsec tip for the red - something that might’ve helped ViceSociety avoid being the subject of this analysis by Unit42 had they known it!
Defensive
🔥VMwareCloak - A PowerShell script that attempts to help malware analysts hide your VMware Windows VM's from malware that may be trying to evade analysis;
🔥Mac Monitor - The latest tool released by Red Canary, it’s essentially like Procmon for macOS - capturing a range of telemetry types to help perform analysis of malicious procedures;
🔥Warpgate - A smart SSH, HTTPS and MySQL bastion host capable of relaying traffic to specific hosts and URLs in your network, recording every session for live review or replay. Honeypots, anyone?
@embee_research has shared another excellent post, this time with a comprehensive walkthrough of his teardown of a RedLine stealer sample;
Kostas Tsale has published a neat tweet summarising analysis steps and CyberChef recipes to help parse the latest Remcos RAT samples;
Check out this wrap-up post by @shellcromancer who completed the 100 days of YARA challenge, focussing on macOS & mach-o binary signatures - an often under-represented area in YARA rules;
🔥Splunk’s Threat Research Team have published a comprehensive article looking at the growing abuse of vulnerable and malicious drivers, highlighting potential mitigations and - of course - some handy Splunk queries to help you surface their abuse;
A YouTube talk for those in Threat Intel - how to measure the value of your work by understanding your stakeholder(s);
If you’re looking to get into Detection Engineering, this list of resources, training, and other miscellaneous links will help you get started on your journey - or at least help you figure out if it might be the right fit for you!
The Australian government has banks and financial services companies in the crosshairs, signalling plans to conduct cyber “war games” to test and improve their cyber response capabilities. Other sectors that may soon take part are operators of critical services such as hospitals, the traffic network, and the banking system;
New to macOS defence/offence? Either way, you’ll need to understand the fundamentals - start with this post on macOS App structures, followed by the second in the series which looks as macOS GateKeeper;
Assistant is a web UI for ChatGPT that can be self-hosted and uses the ChatGPT API - this is particularly useful if you’re worried about privacy concerns, as the API user policy says the prompts won’t be used to train the AI model, unlike in the public web version.