This is an extended newsletter, so it may be truncated towards the end of the email. To read the full post, just select the View entire message hyperlink at the bottom of the email or Open in Browser!
Mark-of-the-Web Bypasses exploited in-the-wild
Per Will Dormann, Senior Vulnerability Analyst at ANALYGENCE - "many Windows security features — [such as] Microsoft Office Protected view, SmartScreen, Smart App Control, [and] warning dialogs — rely on the presence of the MotW to function." Given this, you’d think Microsoft would be more quick to identify and remediate two straightforward bypasses for the MotW protection - but you’d be wrong.
Bypass #1: Crafted files contained within ZIPs
Dubbed by the world renowned Porg-lover and infosec elder, Kevin Beaumont, as “without a doubt the dumbest zero day I’ve worked on,” no more detail has been provided on this bypass other than to say that “any file contained within a .ZIP can be configured in a way so that when it's extracted, it will not contain MOTW markings.”
The lack of additional detail or Detections being shared is due to (well-founded) concerns that prolific actors such as Emotet and Qakbot would subsequently start abusing it at scale in their campaigns. This flaw is present on all versions of Windows from XP onwards.
While Microsoft are figuring out what to do, Acros Security have already released a free, unofficial patch via their 0patch platform.
Bypass #2: Corrupt Authenticode Signatures
Another Will Dormann special, he discovered that files with malformed Authenticode signatures will be treated by Windows as though it didn’t have the MotW. This will work for any file that can be signed with Authenticode signatures such as Javascript and .exe files, and is confirmed to work on Windows 10+ and Server 2016.
Similar to the first technique, this has been observed exploited in the wild in a Magniber ransomware campaign. Microsoft haven’t advised what they’re doing to investigate and remediate this - if anything.
These bypasses are concerning, as MotW underpins crucial user protections offered in Windows, which are the very thing actors have been going out-of-their-way to use disk image files (e.g. .vhd/.iso) to circumvent. Unfortunately this means we can expect more initial payloads to achieve execution on endpoints, so it’s crucial to have alerting in place to catch the behaviours they exhibit when they do.
Internet Explorer still causing trouble from beyond the grave
Researchers from Varonis have revealed two flaws that could be abused to either crash the Event Log application or DoS a target’s hard drive - all thanks to a legacy Internet Explorer log handle with insufficient ACLs that allows anyone to read and write logs to it.
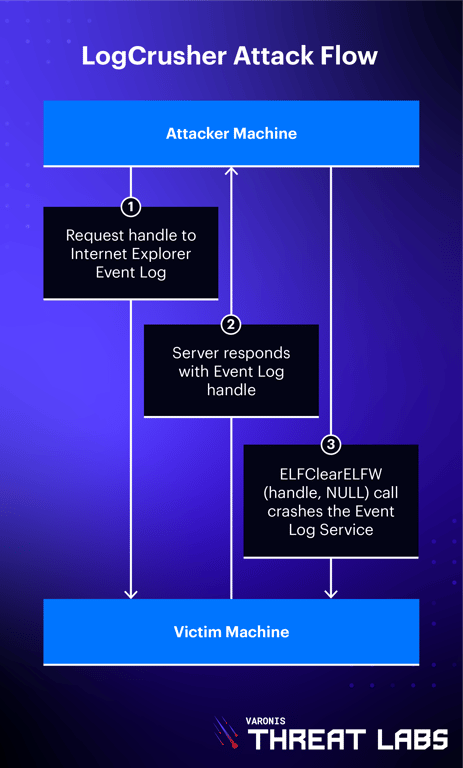
LogCrusher - Crashing the Event Log application
By simply opening a handle to the victim’s Internet Explorer Event Log and providing a NULL BackupFileName value when calling the ElfClearELFW function (traditionally used to clear and backup logs), an remote attacker is able to crash the Event Log on the target machine. While the service will attempt to recover three times on a crash, it will stay down for 24 hours if it fails again on the third attempt.
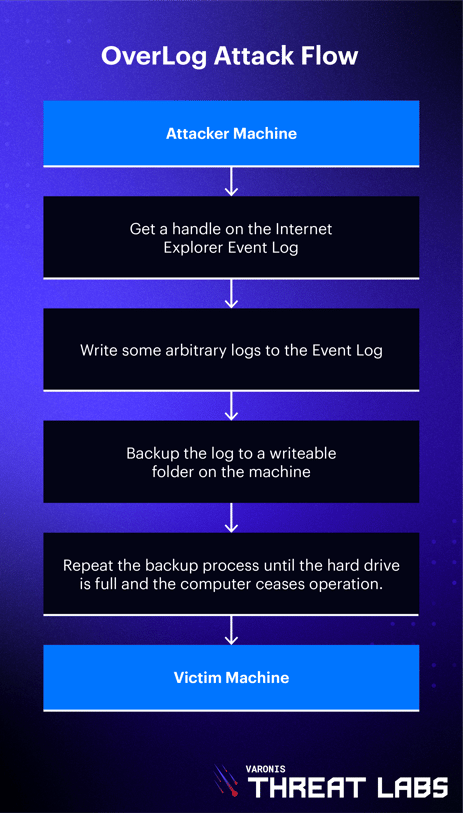
OverLog - DoSsing a remote computer by filling its hard drive
Using the same handle and function as before, an attacker can backup arbitrary logs from the Event Log to a remote, writeable folder on the target machine. Repeating this over and over again will eventually fill up the hard drive to the point where the target is unable to write to the system pagefile, rendering it unusable.
Where to from here?
While Microsoft did issue a “fix” in the October Patch Tuesday update, this was simply to restrict access to the IE Event Log to local administrators. Sure, this does elevate the bar for ease of exploitation, and it’s worth installing this patch to benefit from this change - but does that really offset its utility for an attacker?
LogCrusher allows attackers to disable Windows Event Logging remotely, meaning if they had a foothold and wanted to move laterally through a network - they could first use this to blind logging and any EDR products or alerting that rely on it, before jumping on and dropping their tools. Sounds pretty handy, right?
Consider environments where SOEs are built programmatically, with a default Local Admin account that performs subsequent setup steps (thereby replicating the password throughout the network), or if an attacker compromises an account that’s a member of the domain’s Local Administrators group. These are two very plausible scenarios, which would leave both LogCrusher and OverLog as viable attack vectors for either defence evasion or destructive attacks.
All that said, what Microsoft have done still raises the bar for this attack to be successful. As a result, I’d suggest leaving this as a Low priority for your Detection Engineering team to get to at some point - just don’t ignore it!
DEV-0832, a ransomware nomad using typical TTPs & following the money
Microsoft have profiled DEV-0832, more commonly known as Vice Society. The group have used BlackCat/ALPHV, QuantumLocker, and Zeppelin ransomware in campaigns - all within this year, by the way - and were most recently observed deploying a Vice Society-branded variant of Zeppelin before switching to a modified ransomware payload dubbed RedAlert. Interestingly, Microsoft also noted that in some instances, “the group did not deploy ransomware and instead possibly performed extortion using only exfiltrated stolen data.”
The group’s targeting appears highly flexible, targeting “organizations where there are weaker security controls and a higher likelihood of compromise and ransom payout.” This has previously been local government and retailers, but during July and October DEV-0832 focussed heavily on the global education sector with an emphasis on the US.
Vice Society will be hard to predict, due to their willingness to arbitrarily rotate through multiple ransomware programs - or even not deploy ransomware altogether - and shift their targeting based on whatever industry represents the path of least resistance at the time.
Their flexibility in targeting means it’s best not to fixate on this group as a long-term threat even if you are in the education sector right now, but to capitalise on the fact they use typical TTPs - such as using PowerShell scripts; repurposed legitimate tools; exploits for public vulnerabilities, and commodity backdoors like SystemBC - to deploy detections that would catch not just them, but other actors that share their TTPs as well.
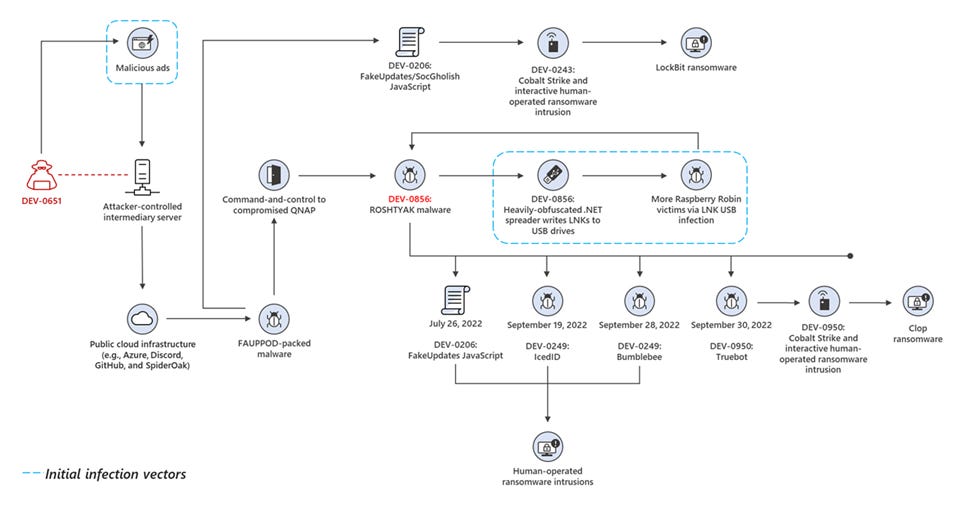
Raspberry Robin - an active threat enabling secondary malware and ransomware infections
Microsoft’s Threat Research team have published another stellar report this week, this time looking at Raspberry Robin (DEV-0856), the USB-borne worm that first emerged in May this year. It appears to be continuing its rapid propagation - appearing in nearly 1,000 organisations over a 30 day period, and expanding its client base for 2nd-stage payload delivery to include IcedID, BumbleBee, and TrueBot.
In a crucial development for our understanding of the threat it poses - Microsoft have reported that several instances involving subsequent deployment of Cobalt Strike (and in some cases, TrueBot) - the compromise has culminated in the delivery of the Clop ransomware. Further instances of IcedID, BumbleBee and SocGholish infections have likewise resulted in the conduct of human-operated ransomware intrusions.
Since first emerging as what appeared to be worm propagated without a clear purpose, we now known Raspberry Robin can be expected to facilitate deployment of any one of a number of secondary malware families, and potentially enable the execution of ransomware infections.
Microsoft further shed light on the potential entry vectors for the malware, noting that a family of packed malware dubbed “Fauppod” had been delivered via a malicious ad campaign operated by an actor tracked as DEV-0651 - this went on to drop a heavily obfuscated .NET dll, which is believed to be the earliest known source for a Raspberry Robin infection.
All this goes to show that Raspberry Robin operates within a much broader cyber criminal ecosystem that involves numerous, actors, malware, and ransomware families - reinforcing the need to monitor this as a serious threat.
Cranefly - Smuggling C2 in IIS Logs
The cyber espionage-motivated actor Cranefly (UNC3524) has been seen employing a new dropper they signature as Trojan.Geppei. Geppei monitors IIS logs for specific keyword strings that’ll indicate if it’s meant to either install new malware (“Wrde”), execute a command (“Exco”) or drop a tool to disable IIS logging (“Cllo”).
The two pieces of malware it might drop are ReGeorg - a known web shell that can create a SOCKS Proxy for the attacker to use; and Danfuan - a newly discovered in-memory backdoor.
While this technique is noteworthy for its ability to hide C2 communications amongst the huge volume of traffic hitting IIS servers, your bread-and-butter IIS detections will still give you decent visibility of subsequent tasking being executed.
In instances where the Geppei implant is tasked to deploy new malware or disable IIS logging, a payload must be written to disk. Looking for the IIS worker process (w3wp.exe) writing files with executable extensions to disk, for example, would pick this up.
Other Reporting
A joint advisory by US security agencies has warned of “Daixin Team” - a ransomware and data extorsion group targeting US healthcare organisations by popping unpatched VPNs and abusing stolen credentials;
South Korean research outfit S2W have shared research examining recent attacks using Android malware by North Korea’s Kimsuky threat actor;
AhnLab’s ASEC have published a detailed analysis of the evolution of Magniber Ransomware TTPs, spanning May - September this year;
Trend Micro’s profile of BlackCat ransomware is one worth reading and slapping a bookmark on for future reference;
The Fodcha DDoS botnet has continued to grow since being first identified in April 2022, hitting an average of 1,000 targets each day by drawing on a network of 60,000 active bots capable of pushing up to 1 TB/s of traffic. The group extorts victims for Monero - currently valued at ~$1,500 - by embedding ransom demands in the packet dataframes.
CloudSek have flagged the sale of exploits for the RCE vulnerabilities CVE-2022-26500, CVE-2022-26501, and CVE-2022-26504 in Veeam Backup & Replication on the XSS Dark Web forum;
Critical RCE vuln in VMWare products gets a patch...and a PoC exploit
VMWare have released patches for a vulnerability in Cloud Foundation and NSX Manager appliances that would enable remote code execution - as root - on vulnerable instances.
The vulnerability (CVE-2021-39144) stems from a flaw in the open-source XStream library used in both solutions, and was considered serious enough that Cisco are porting patches for some end-of-life products.
The researcher who discovered the vulnerability also shared a write-up and PoC code that will provide the attacker a root shell. This was nearly a week ago, on the 25th October - so make sure you’ve got your patched either in place or on the way!
CVE-2022-35737 - an SQLite RCE/DDoS vulnerability that’s old enough to buy you a beer
Researchers at Trail of Bits have discovered a vulnerability (CVE-2022-35737) spanning all versions from SQLite 1.0.12 (released October 2020) through 3.39.2 (released July 21, 2022) that could provide attackers code execution on 64-bit systems.
This is possible in binaries compiled without stack canaries - in instances where stack canaries are present, an attacker can still conduct a DoS attack on the vulnerable instance.
Given the widespread use of SQLite for back-end database storage in programs and Apps running on Android, iOS, Windows, macOS - and even browsers such as Chrome & Firefox - this is one to consult with Dev teams and product owners on, to ensure you’re able to identify all vulnerable instances in your organisation’s code base.
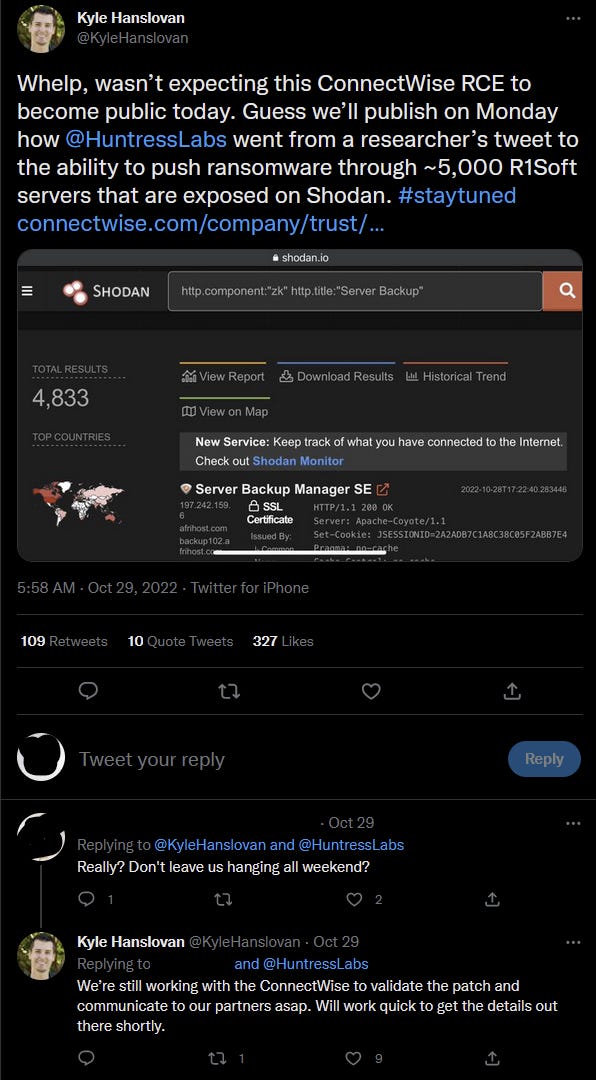
Patch for Critical ConnectWise vulnerability released early, without context
A Critical security update has been issued to patch vulnerable instances of Managed Service Provider ConnectWise’s Recover (<v2.9.9) and R1Soft Server Backup Manager (v.6.16.4) products, with no further context provided other than to note that vulnerabilities existed which “could allow the ability to execute remote code or directly access confidential data.”
The prioritisation of the security update also denotes the vulnerabilities “are either being targeted or have a higher risk of being targeted by exploits in the wild.”
Crucially, @KyleHanslovan of Huntress Labs, who flagged the unexpected release late Friday afternoon in the US, noted that the flaw could have potentially allowed an actor to “push ransomware through ~5000 R1Soft servers that are exposed on Shodan.”
It’s also particularly concerning that he noted they’re “still working with […] ConnectWise to validate the patch and communicate to [their] partners asap” - indicating that ConnectWise likely jumped the gun. Touch wood it’s not because the hypothetical ransomware scenario became reality.
Other vulnerabilities
Apple has issued a security update to address CVE-2022-42827, which would have allowed an attacker to execute code with kernel privileges on vulnerable iPhones and iPads. Worth noting - Apple say the flaw “may have been actively exploited”;
Not to be left out, Google have also patched an 0-day in Chrome that’s been exploited in-the-wild. Google haven’t gone into detail on how it works or what it grants an attacker, other than to reveal it’s a type confusion bug. The impact of these bugs can range from reading information from other apps, to execution of arbitrary code;
Cisco have released a security advisory that includes a notification of a vulnerability (CVE-2022-20822) in it’s Identity Services Engine (ISE) product that would allow an authenticated, remote attacker to read and possibly write to restricted files. The vulnerability currently has no patch or workaround - with the earliest planned fix coming in November;
Several flaws in Juniper Networks appliances have received patches, the most noteworthy being CVE-2022-22241, which could enable RCE on a vulnerable instance;
CISA have added two vulnerabilities in Cisco’s AnyConnect Secure Mobility Client for Windows from 2020 (CVE-2020-3433 and CVE-2020-3153) to their Known Exploited Vulnerabilities list. This was followed by a warning from Cisco that confirmed their exploitation in-the-wild - unsurprising given publicly available PoC exploits exist for both of them. The flaws would allow an attacker to perform DLL hijacking that enables arbitrary code execution with SYSTEM privileges.
Offensive
Nginxpwner - a tool that scans for common nginx misconfigurations & vulnerabilities;
Spartacus - a DLL Hijacking discovery tool that can parse raw PML log files from ProcMon;
Artfuscator - add flair to your malware and troll malware analysts by manipulating the binary’s control graph to any image if your choice;
Google’s CSP Evaluator tool will parse any Content Security Policy Header you provide it, highlighting misconfigurations and vulnerabilities. Hm, I wonder what a Pentester/bug bounty hunter might use that for?
In case anyone’s on the fence about how comprehensively the LastPass browser extension has been proven insecure - here’s a video walkthrough of a custom Cobalt Strike plugin made by Scott Nusbaum of TrustedSec pulling even password-secured credentials from the LastPass Vault;
The team from Praetorian have shared a walkthrough of a novel attack path, looking at how to pivot from a compromised Github personal access token into an internal environment, by using Github Actions as an initial launch point;
MDSec continue to publish great content - this here is a write-up of them taking the AutodialDLL persistence method to the next level, creating a PoC that pairs it with an SSP to scrape NTLM hashes from the lsass process;
Google’s Project Zero have revisited risks posed by continuing to use the RC4 stream cipher with Kerberos authentication, sharing this post exploring an RC4-MD4 downgrade attack, how it works, and how to exploit it;
If you can replicate this on your next Red Team engagement, beers are on the whoever signed the risk acceptance for CVE-2018-6606 - how to get execution as SYSTEM with a Macro-enabled document;
If you’re looking to learn Chrome browser exploitation, this detailed post - the first in a 3-part series - will walk you through how to do just that.
Defensive
Locksmith - a tool to help identify & remediate common misconfigurations in Active Directory Certificate Services;
upx-recovery-tool - a script that attempts to repair common modifications done by malware creators to ELF UPX-compressed files, in order to prevent their automatic unpacking with a standard UPX tool;
text4shell-tools - a tool to help you scan for installations vulnerable to the much-hyped Text4Shell vulnerability from last week;
Fox-IT have published v1.0 of their seriously impressive dissect.cobaltstrike tool, adding support for parsing and decrypting Cobalt Strike C2 traffic from PCAP files and also Beacon Client support - allowing you to connect to a Cobalt Strike Team Server and receive tasks and send back data like a real Beacon;
TypeRefHash is a .NET equivalent of ImpHash, because - TIL - ImpHash doesn’t work with .NET binaries!
@inversecos has pushed another great DFIR post, this time looking at recovering cleared Chrome Browser history;
Jason Reaves from the Walmart security team has published this detailed walkthrough of his process for dumping the config from a Brute Ratel agent;
Florian Roth has merged the private feed and community Sigma ruleset to Valhalla - your one stop shop for YARA and Sigma rules;
An updated (10-10-2022) YARA rule to detect RaccoonStealer 2.0 payloads;
This is a great post by Alex Teixeira, looking at a discussion pretty much every SOC or Security Engineering team that manages a SIEM will encounter - how do we manage our SIEM license, do we push to a Data Lake? How do we query it - do we even need to? What do we push to the SIEM vs the Data Lake?
Make sure you’re looking out for malware punching holes in Windows Firewall - here’s how;
Tony Lambert’s taken a look at carving PE files out of the guff malware authors can pad them with to bypass size limits on email/network filtering appliances - this time using Foremost;
Advanced Microsoft Authenticator features have hit general availability, including number matching and additional context in MFA push requests - these are critical steps that’ll make it significantly harder for attackers to execute MFA Fatigue attacks to bypass your MFA protections, so it’s worth looking to implement these if you can.
Australia continues to be battered by cyber attacks and data breaches - the latest of which was Australian Clinical Labs (ACL) who were hit with Quantum ransomware back in February, but only just disclosed the breach of 223,000 sensitive customer records and diagnoses on Thursday - eight months after the incident occurred;
Cisco have shared their Quarterly report for Q3 2022, noting Remote Access Software and stolen credentials continue to be a prominent means of initial access, while also highlight a need for organisations to be more vigilant in deactivating user accounts on departure, and to adopt MFA as part of their security baseline;
CERT-EU, the EU agency that provides incident response to official EU agencies, said that almost two-thirds (63%) of the threat alerts it sent in Q3 2022 were related to cyber-espionage activity;
Coveware have released their Q3 report on the state of ransomware - BlackCat, Hive, and Black Basta are the 3 most observed ransomware variants, and while both the average and median ransomware payments have climbed on last quarter to $258,143 and $41,987 respectively, they’re still well below the peaks seen in Q4 2021.
Some nice stats for your next report on supply chain risk - Blackberry have found that 80% of organisations surveyed have been notified of either a vulnerability or attack on in their software supply chain over the preceding 12 months, with over 50% experiencing disruption or loss of data, intellectual property, or reputation.
In case you missed it, see our recent post exploring the lessons learned from the Medibank Incident Response efforts, and providing an overview of the changing threat landscape that Australia is increasingly finding itself the center of: