Emotet arcs up again after 3 months
As unfortunate as it was inevitable, Emotet has once again returned from a short hiatus this week, delivering a burst of Phishing lures through its Epoch4 botnet.
The Emotet-hunting collective Cryptolaemus were the first to spot the pickup in activity, with TA542 again using their Red Dawn template to deliver inflated (~500MB) macro-enabled Word documents via invoice-themed Phishing emails.

The Word documents are contained in a password-protected archive, and use malicious macros to download the Emotet payload - a similarly bloated dll file, designed to bypass automated scanning solutions that typically can't process large files.
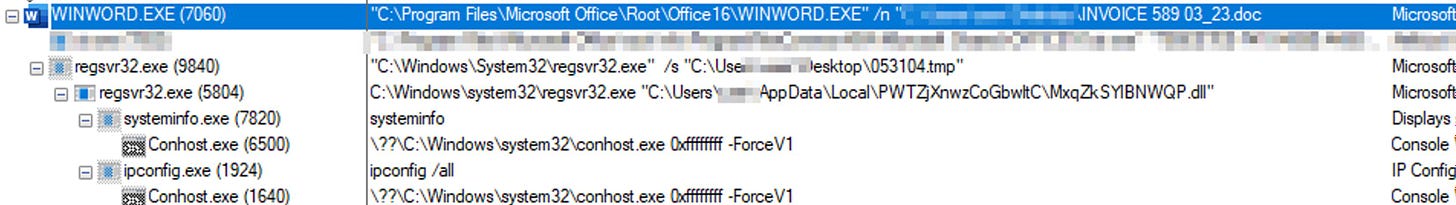
The dll is run via the native regsvr32.exe binary, performing basic system enumeration actions using systeminfo and ipconfig.
Macros? What year is it?!
Emotet’s use of macro-enabled documents was a particularly strange choice given Microsoft has been blocking macros by default in downloaded documents since mid-2022.
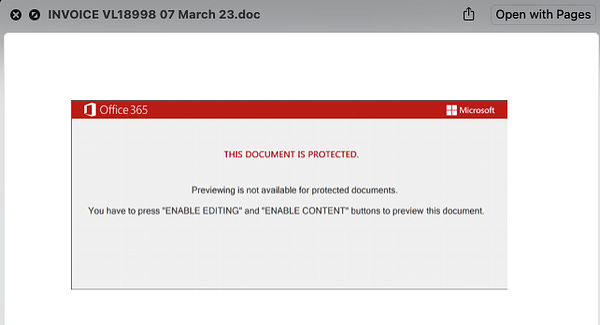
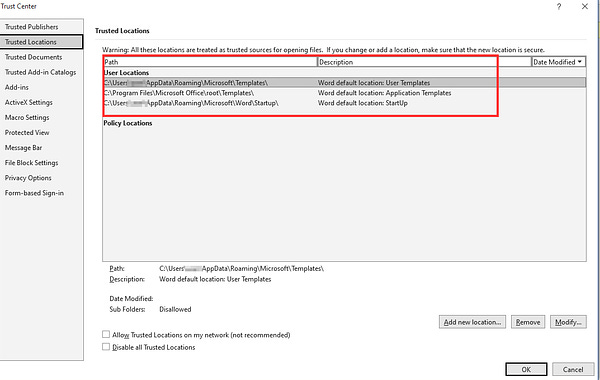
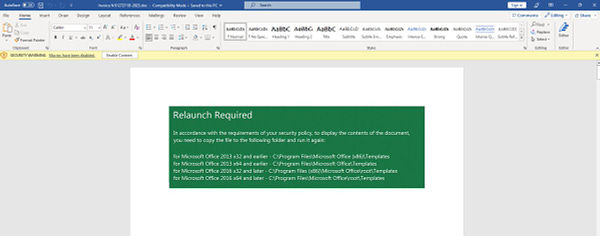
While it may have raised eyebrows initially, TA542 seem to have quickly realised their mistake and added a step in the execution chain, prompting the user to copy the maldoc into a Trusted Location in order to run. Doing this will bypass Microsoft’s Mark-of-the-Web protections, allowing the user to click Enable Content as usual to execute the malicious macros.


Memes make the world go ‘round
One of the best things about infosec is that the majority of us are world-class piss-takers and meme-makers, and Brad Duncan provided a prime example this week. Bone Apple Tea:
Automated MFA bypass and Session Token theft the new norm for Android malware
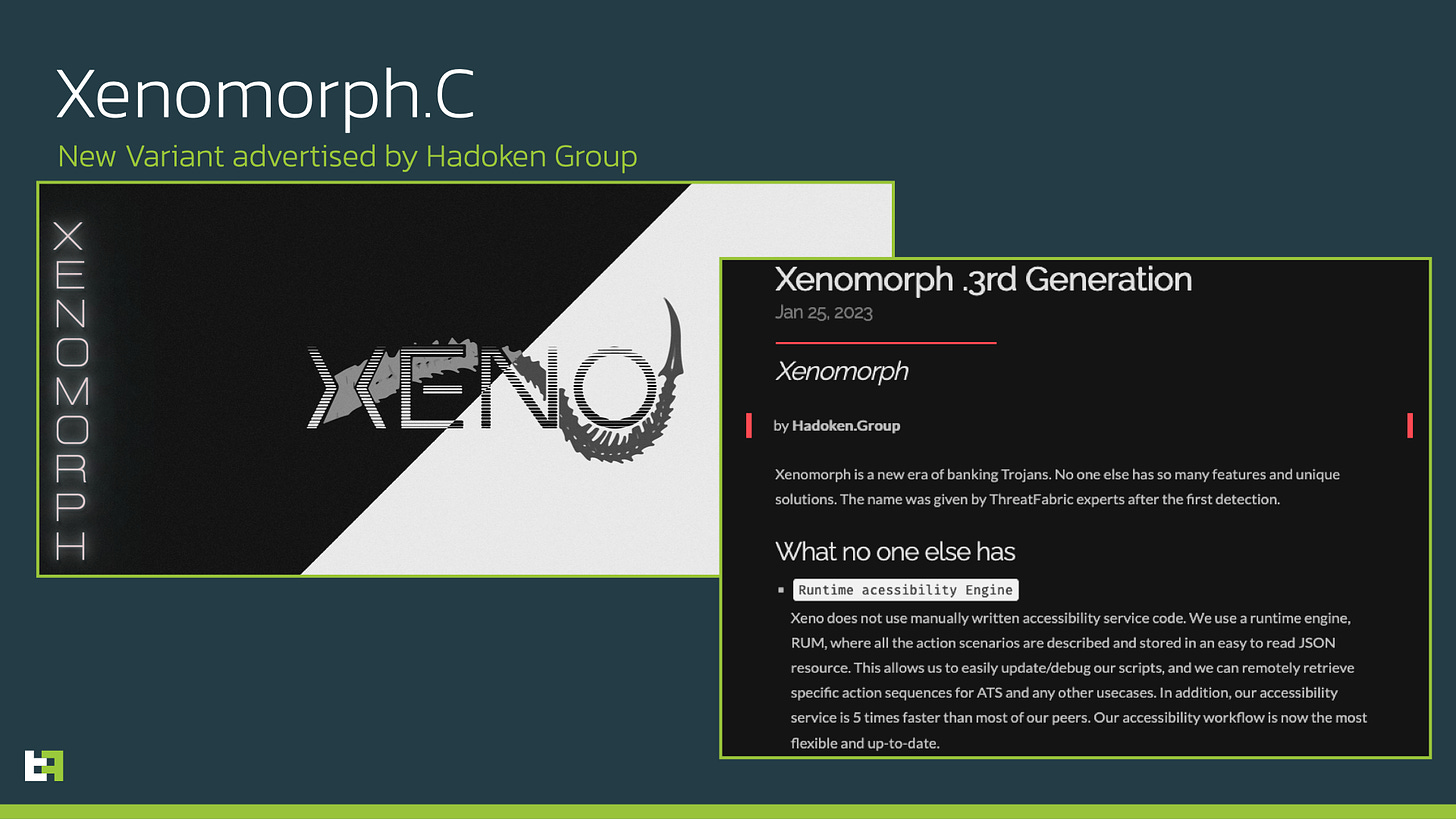
Researchers at Threat Fabric have reported on a new and improved version of the Xenomorph Android banking malware which was released in late January, and added significant capabilities which elevated it to the level of more mature offerings such as Gustuff and SharkBot.
The new variant adds targeting support for hundreds of new banks and financial institutions - including several cryptocurrency wallets - and a modular script-based “runtime engine” that allows it to emulate various sequences of user interaction as part of what is known as an Automated Transfer System (ATS).
New capabilities
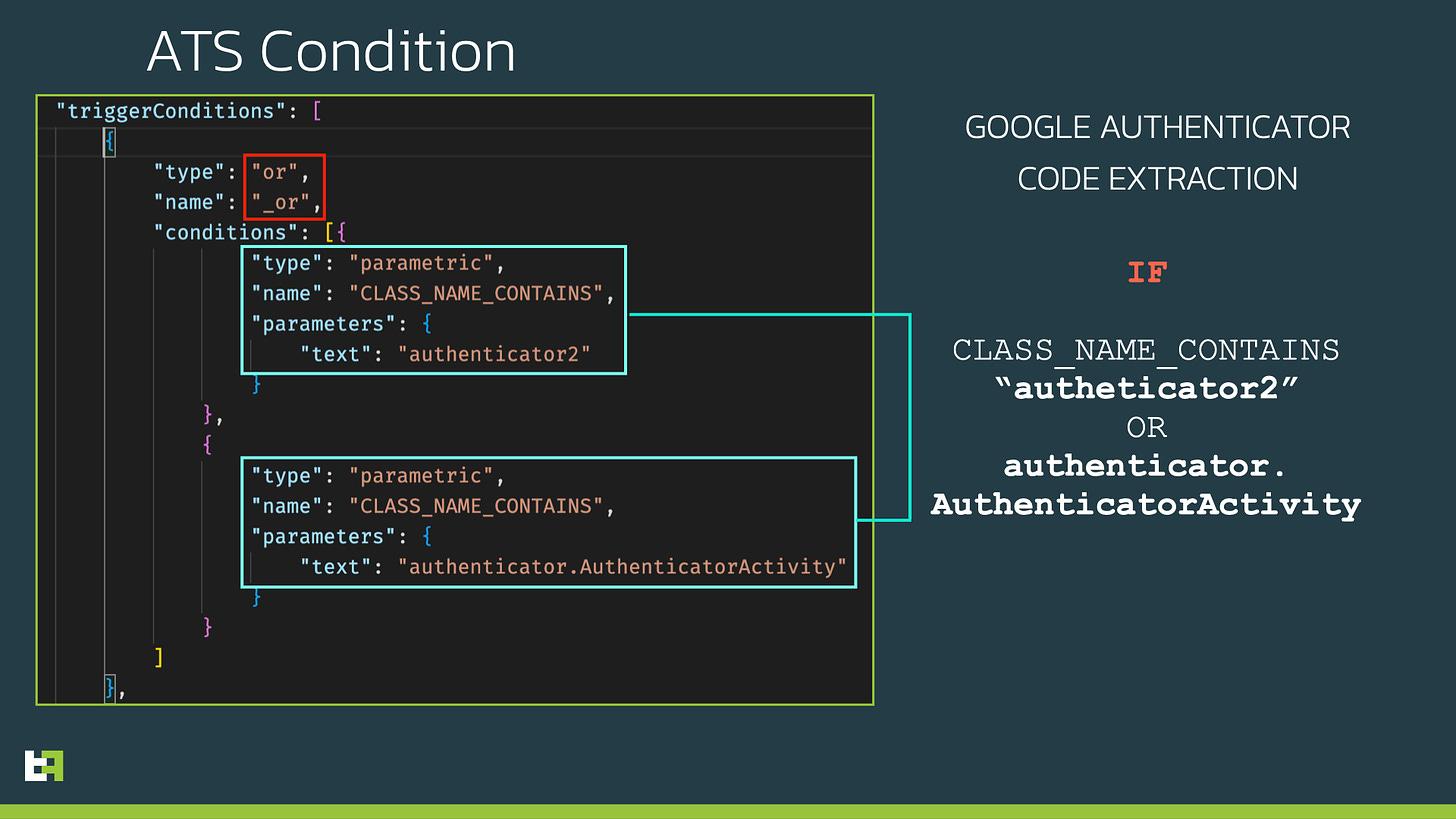
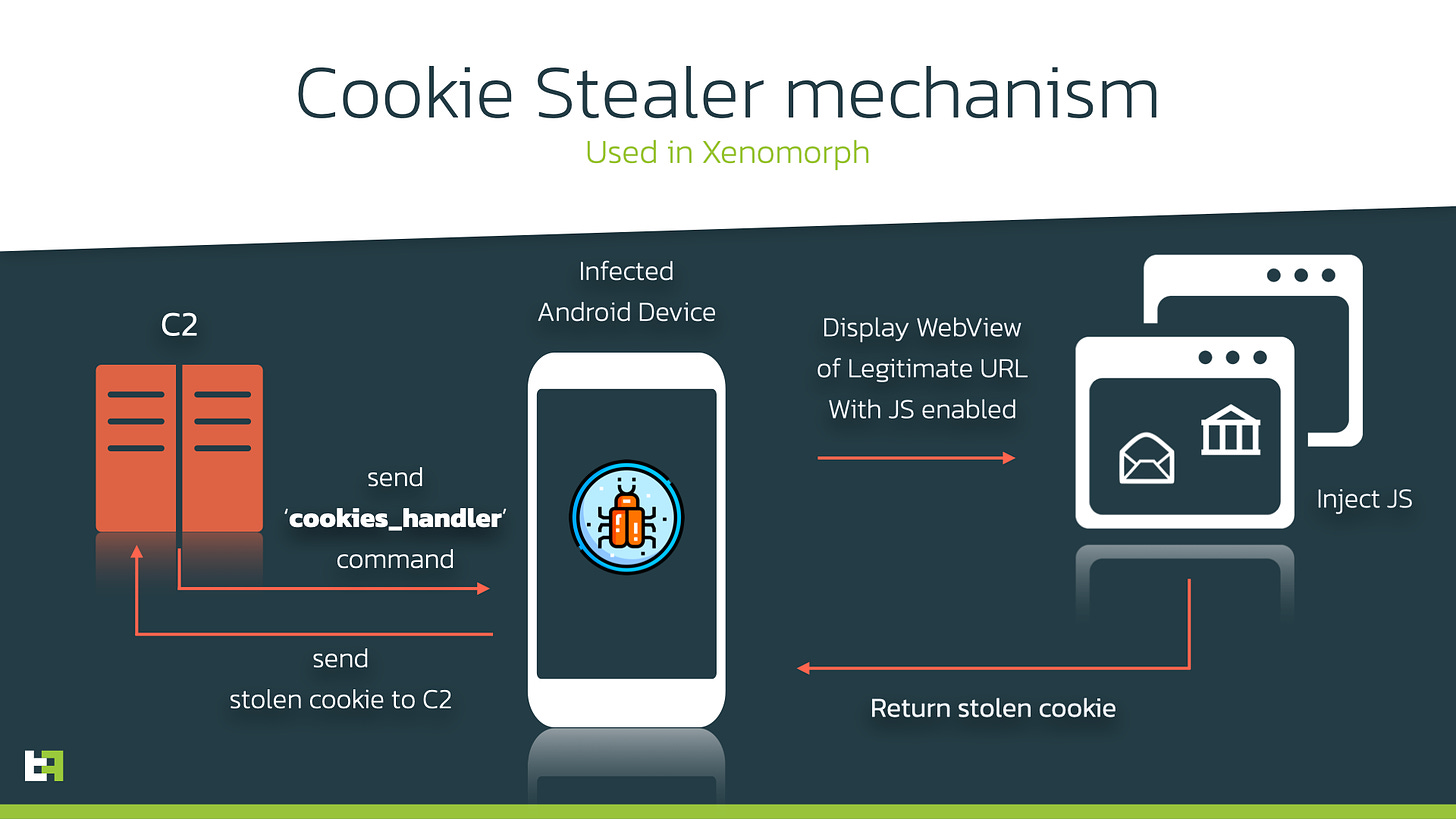
Xenomorph’s implementation of an ATS is unique in its use of scripts that allow operators to configure conditional execution and prioritisation of actions to be performed by the malware.
This is used, for example, to have the MFA Code collection module trigger every time the Google Authenticator app is launched as part of the malware’s operation, thereby enabling the seamless circumvention of MFA-protected applications.
If bypassing MFA protections wasn’t enough, a Cookie Stealer module was also added. This works by socially engineering users into authenticating to a service and generating a Session Token, which is then extracted and sent back to the operators to perform account takeovers.
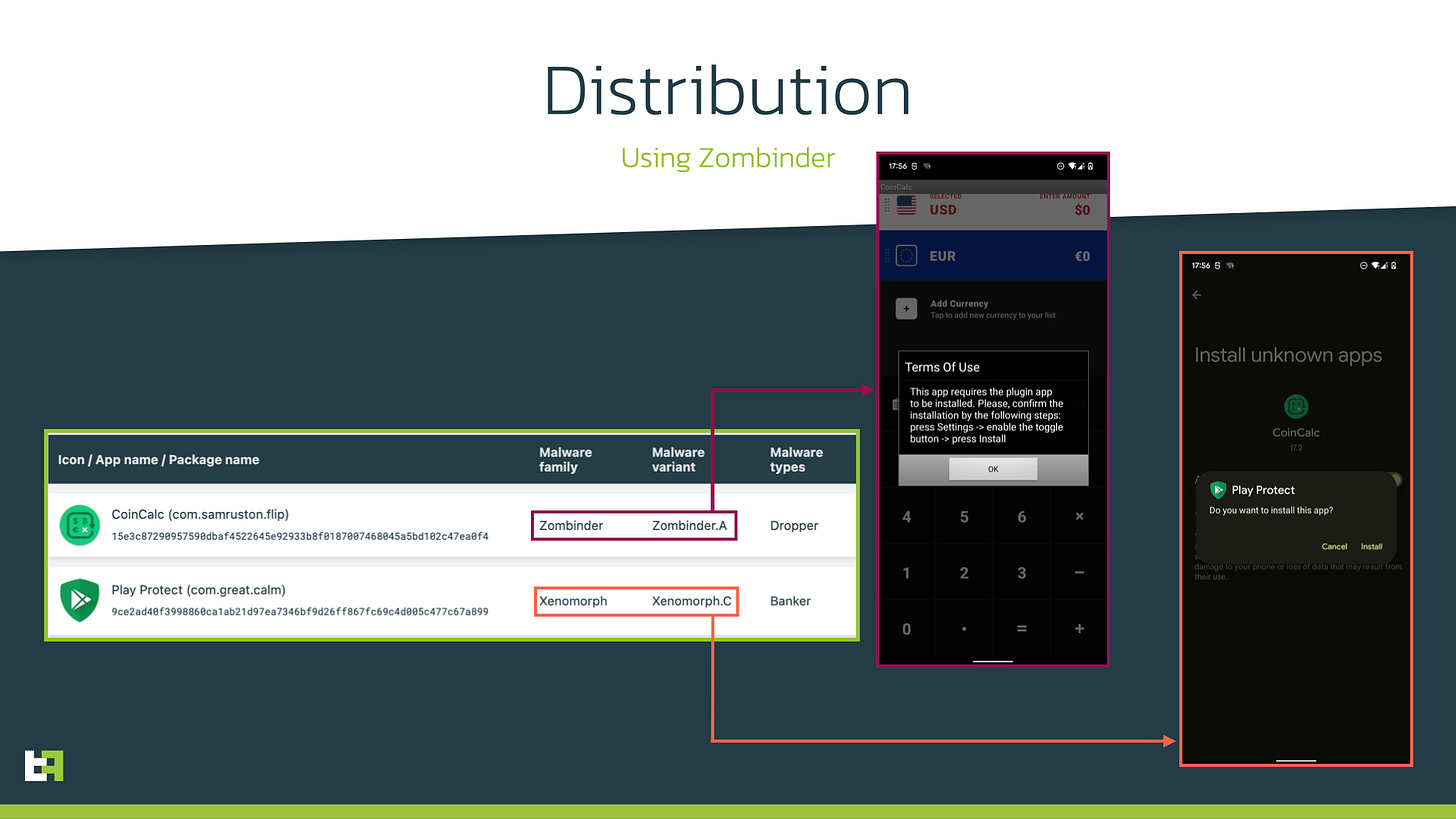
Use of the Zombinder dropper service
After previously using the GymDrop and BugDrop programs for distribution, Xenomorph’s developers - who go by the name of Hadoken Security Group - have started using a popular 3rd-party “APK binding” service offered on the Dark Web called Zombinder to deliver their latest variant.
This works by essentially backdooring a legitimate app - in this case a currency converter app - which operates as intended but later delivers the malicious payload masquerading as an update.
Don’t sleep on Mobile Malware
Mobile Banking Malware rarely gets the same level of attention as their desktop-bound counterparts, which has allowed their developer ecosystem to thrive to the point where automated bypassing of MFA protections and theft of Session Tokens is almost an entry-level feature.
The impact they have may not make the headlines that ransomware does, but it’s clear that this is a threat that is not to be taken lightly. While traditional use cases have been to pilfer funds or hijack personal accounts, the technical maturity already exists for this to be leveraged for more ambitious purposes.
As a thought exercise, ask yourself - what’s to stop ransomware, or even state-backed actors from using it to steal a Session Cookie for a company’s m365 tenant, or pairing the MFA extraction module with a Credential Stuffing attack, for example?
DRPK targets media orgs with LinkedIn lures and the latest techniques
Mandiant have published a two-part report on a campaign conducted by UNC2970, which they attribute with high confidence as TEMP.Hermit - a highly capable threat group operating out of the DPRK’s 3rd Bureau, responsible for conducting foreign intelligence operations.
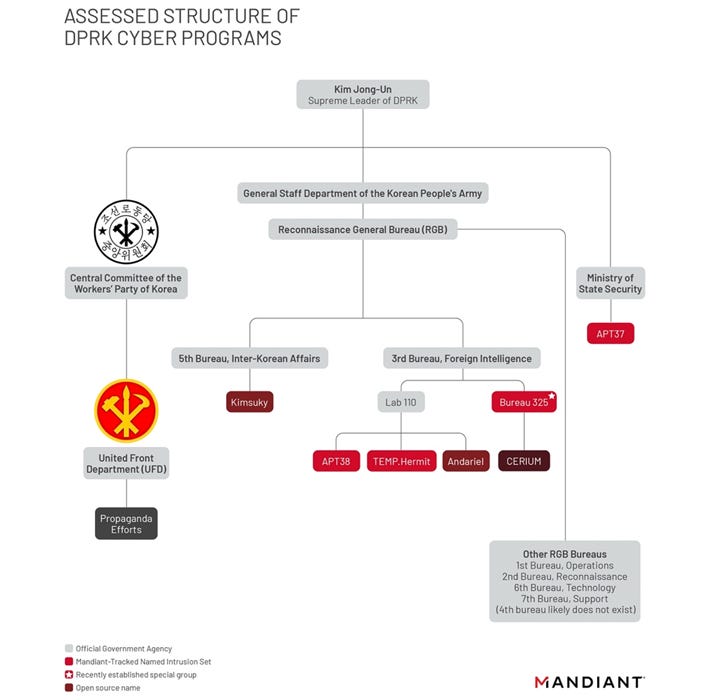
The report, broken out into Part 1 and Part 2, is packed with information and well worth reading on their own. If you’re on the fence or short on time, here are a few key points from the reports:
UNC2970 activity has significant overlaps with the sophisticated Operation Dream Job/Operation AppleJeus campaign of 2021/22 that targeted over 250 individuals in the media, IT, cryptocurrency and fintech industries;
The campaign leaned heavily into social engineering, with victims contacted via a set of highly curated LinkedIn personas and drawn into engaging in further conversation over WhatsApp to build rapport with their targets;
Macro-enabled Word documents that performed template injection were then delivered via email or WhatsApp, masquerading as a tailored job description based on the target;
The actors used a PLANKWALK backdoor to import and execute 2nd-stage loaders, as well as Microsoft’s InTune MDM solution to deploy a shellcode downloader;
A range of new tooling was seen in this campaign including TOUCHSHIFT (payload dropper); TOUCHSHOT (screenshot plugin); TOUCHKEY (keylogger); HOOKSHOT (C2 tunnel using TLS1.0); TOUCHMOVE (loader), and SIDESHOW (backdoor that communicates over HTTP);
The attack paired an in-memory only dropper (LIGHTSHIFT) with a host-specific, VM-Protected payload (LIGHTSHOW) to leverage the BYOVD technique and circumvent EDR protections.
This is a particularly interesting campaign as it demonstrates the substantial variety of custom malware that DPRK actors have at their disposal. Moreover, their abuse of Microsoft InTune to deploy payloads and the BYOVD technique to bypass EDR protections reinforces a previous Proofpoint report that found North Korea’s cyber workforce are quick to adopt and experiment with emerging tradecraft.
Two-year Chinese campaign abused vulnerable SonicWall appliances
A joint investigation by Mandiant and SonicWall has uncovered a long-running campaign perpetrated by a suspected Chinese actor, tracked by Mandiant as UNC4540.
The actor targeted unpatched SonicWall Secure Mobile Access (SMA) appliances, deploying a series of bash scripts and a variant of the TinyShell backdoor to siphon credentials and maintain access to the compromised environment. Mandiant noted the deployed capability clearly demonstrated the actor possessed a “detailed understanding of the appliance” and their capabilities were “well tailored to the system to provide stability and persistence.”
Abuse of external-facing appliances is a well-documented TTP favoured by Chinese actors, and used to great effect. This campaign is just the latest example that highlights it as trend to watch out for, as it’s unlikely to go anywhere soon.
So, what needs patching?
While the report refrains from mentioning specific vulnerabilities, its recommendations are aimed at owners of SMA100 appliances, urging them to upgrade to a version of 10.2.1.7 or higher in order to benefit from additional hardening measures.
There were a total of 24 vulnerabilities discovered in SonicWall’s SMA100 product over the past five years, including five Critical severity vulnerabilities - almost all of which were rated with an eye-watering CVSS 9.8 score.
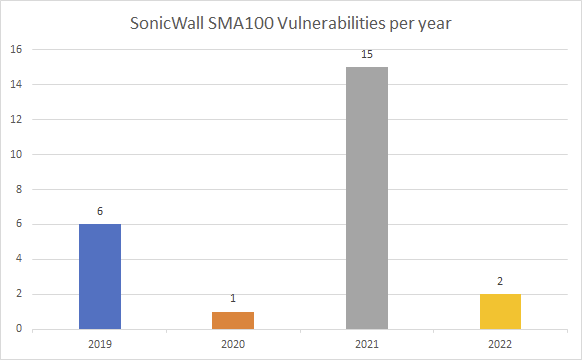
With numbers like these, it’s no wonder that Chinese threat groups have gravitated towards exploiting public flaws in internet-facing systems.
In lieu of any specific vulnerability being fingered as the root cause of the compromises, it’s worth - at a minimum - ensuring your SMA100 appliances are at the patch level recommended in the advisory.
Other Reporting
Check Point researchers have published a report on a long-running, espionage-motivated campaign by the Chinese Sharp Panda group which targeted government entities throughout Southeast Asia. In particular, the report highlights the ongoing development of the Soul malware framework which was first seen in 2017, and supports numerous features including a “radio silence” mode that specifies blackout periods for communication, presumably to evade detection by only running during the target’s business hours;
Threat Intelligence vendor EclecticIQ have tentatively attributed a recent campaign distributing the KamiKakaBot loader to victims in the ASEAN region as the work of the Dark Pink APT group;
🔥The DFIR Report have released their 2022 retro report, which does a fantastic job of breaking out key tools and techniques used by various prolific Initial Access threats such as Qakbot, Emotet, and IcedID;
🔥Researchers from Lumen Black Lotus Labs have uncovered HiatusRAT, a novel malware family being distributed in a campaign targeting DrayTek routers; capable of sniffing network traffic, acting as a SOCKS5 proxy for forward-deployed implants, and downloading additional payloads;
First seen in December last year, the Nevada ransomware program has been flagged as an apparent variant of the Rust-based version of the Nokoyawa ransomware, based on technical overlaps in their code;
SentinelOne reports that the IceFire ransomware - first seen in early 2022 - has developed Linux payloads that it observed deployed as part of intrusions targeting media and entertainment organisations across the world. The infections were enabled by exploiting CVE-2022-47986 - a critical vulnerability in the IBM Aspera Faspex file sharing software;
🔥Esentire’s Threat Response Unit has surfaced a BatLoader distribution campaign that leverages Google Ads for fake software downloads to deliver a convoluted Python-powered infection chain which ultimately downloads and installs either Vidar Stealer or Ursnif payloads;
🔥Researcher Germán Fernández shared an interesting finding last week - TA577, the distributor of the BB Qakbot botnet, was dynamically generating JavaScript payloads with unique hashes that went undetected on VirusTotal and modifying compromised websites to resolve to a series of DigitalOcean IP addresses that served secondary payloads;
Speaking of Qakbot, Trellix has published a detailed report on Qakbot’s use of OneNote lures in their campaigns - though it appears it may have come a little too late as it was last seen used on March 3, with more recent campaigns reverting to the trusty HTML Smuggling technique;
Morphisec have published a report on a campaign they’ve tracked which leveraged Google Ads and fake Facebook profiles to deliver the SYS01 Stealer, which goes on to steal login data, cookies, and Facebook ad and business account information;
Cisco Talos have warned of the recent spread of the recently updated Prometei botnet, which spreads via RDP, SSH, or SMB; utilises a self-updating mechanism, and leverages DGA-generated C2 domains for communication;
GoBruteforcer is a new Golang-based malware uncovered by Palo Alto’s Unit 42, which targets web servers running phpMyAdmin, MySQL, FTP and Postgres. The malware attempts to brute force accounts using weak or default passwords, and also acts as a stager of sorts, creating an IRC bot on the victim server and awaiting additional tasking.
Credential disclosure vulnerability in Veeam Backup Software
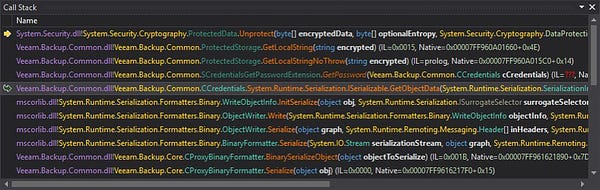
Veeam have issued an advisory urging administrators to patch CVE-2023-27532 - a vulnerability present in all versions of their Backup & Replication product which would allow a remote, unauthenticated attacker to retrieve encrypted credentials from the Veeam.Backup.Service process that listens on TCP/9401.
The stolen credentials could potentially result in the attacker gaining access to the backup infrastructure hosts.
In-the-wild exploitation may come sooner than expected, with a security researcher already able to reproduce an exploit based on the advisory notes. Worse yet, their PoC and subsequent comments indicate the credentials may in fact be dumped in plaintext:

Patches released for critical code exec/DoS vulnerability in Fortinet kit
Fortinet has published an advisory urging admins to patch a CVSS 9.3 vulnerability impacting its FortiOS and FortiProxy product line, which can be exploited by attackers to execute arbitrary code or brick the GUI through a DoS attack.
The Bleeping Computer wrap-up article for this also highlights the urgency of patching, given that the recent RCE vulnerabilities in the FortiNAC and FortiWeb products were exploited within six days of their release.
While it underscores the point of the UNC4540 news article nicely, it’s worth noting that this was enabled in no small part by security research company Horizon3 releasing a weaponised PoC just two business days after the vulnerability was disclosed.
Tweet-sized PoC for MS Office Vuln
A PoC exploit was released early last week for CVE-2023-21716, a CVSS 9.8 vulnerability in Microsoft Office that could enable code execution through a maliciously crafted RTF document.
Users don’t even have to open the malicious document in Microsoft Word - simply viewing it in the preview pane would trigger the vulnerability.
After sharing his independent write-up of the vulnerability, the researcher then pared the exploit code back to fit into a tweet:

This vulnerability impacts versions of Office from 2007 through to Office365, and given how simple it would be for actors to integrate this exploit into their Phishing campaigns, it’s well worth making sure your enterprise endpoints are patched against this!
Other Vulnerabilities
No-interaction RCE Android bugs get patched
Google has released two patch levels for Android Operating System versions 11 through 13, with the earlier release - 2023-03-01 - containing two Critical RCE vulnerabilities worth noting.
The vulnerabilities, tracked as CVE-2023-20951 and CVE-2023-20954, stem from flaws in the Android System component.
Google have been cryptic in their advisory, simply noting that “the most severe vulnerability” could enable RCE without user interaction - without clarifying which of the two Critical-rated vulnerabilities it was in reference to.
VMware Cloud Foundation bug under active exploitation
The 2021 vulnerability (CVE-2021-39144) in VMWare’s Cloud Foundation (NSX Manager) product has been exploited over 40,000 times in the last two months, according to cyber security company Wallarm, and would allow attackers to execute code as root on the vulnerable appliance.
Given the volume of attacks and existence of public PoC exploit code, CISA have added it to their KEV in order to ensure US Federal Agencies are patched against this vulnerability.


With all that said - it might be worth doing a quick check of your own deployment to make sure this one is patched, and didn’t slip past the keeper!
Offensive
Nmap-Peek - A VSCode extension that visualises XML-formatted nmap results in a handy tree format in the sidebar;
🔥Check out this awesome write-up where a Red Team abused HTTP Request Smuggling to harvest AD credentials to access Outlook Web Access (OWA) and subsequently to establish persistent access by migrating clients to a rogue MitM Exchange server;
NetSPI have shared a detailed walkthrough of how to pivot through an AWS organisation, looking at the level of access afforded by leveraging AWS’ IAM Access Analyzer and IAM Identity Center;
Grzegorz Tworek has published a v2 of his OfflineAddAdmin PoC that will - as the name suggests - create a backdoor user account with Admin privileges by booting to a Windows Installer image and manipulating the SAM database of the target system while it’s offline;
🔥IBM’s Intelligence team have kicked off their series looking into Cobalt Strike’s Reflective Loaders with this post, which goes into great detail on the limitations, design, and mechanics that underpin the reflective loading process;
I rarely see lists or articles for physical penetration testing tools and techniques, so make sure you bookmark this one for future reference!
Defensive
Racoon_config - A tool that scans a list of Raccoon Stealer servers listed in the Tria.ge sandbox engine and extracts the config as JSON;
Crawlector - A threat hunting framework designed for scanning websites for malicious objects;
Malware analyst Gameel Ali has shared a script to help decrypt the encrypted strings of the recently uncovered Stealc infostealer;
Elastic have published a new detection for the recently released LocalPotato privilege escalation technique. While it’s written for Elasticsearch instances, the logic used is pretty clear and should be able to be ported to KQL/SPL without too much effort;
Lina Lau (@inversecos) has shared another excellent DFIR write-up, providing a succinct summary of the Azure artefacts to review when responding to an incident targeting an organisation’s Azure environment;
Alex Teixera has published another great post that breaks down the Detection Engineering pipeline, in particular calling out the importance of Detection Research as a part of the process;
If you’re still not sure what protections you have in place for malicious OneNote documents, it’s worth reviewing this article to check and implement some of the great suggestions there - it’s still going around, albeit in much lower volume.
A study conducted by an economics professor in Australia has found that a significant portion of organisations either delay or abstain altogether from disclosing breaches to the media or ASX, pointing to the lack of a formal requirement to report cyber attacks as the reason for this;
Proofpoint researchers have shared their analysis of a…highly unorthodox Russian influence Op conducted by TA499, which attempts to coax “prominent businesspeople and high-profile individuals” that have supported Ukraine or criticised Russian disinformation efforts into partaking in a video call in which the actors try to “catch [them] in embarrassing comments or acts”;
Core members responsible for distributing the DoppelPaymer ransomware were arrested early last week in a coordinated law enforcement operation conducted in Germany and Ukraine;
The administrator and sole retailer of the NetWire Trojan - which is marketed as a legitimate remote management tool but has been widely abused by cyber criminals since at least 2014 - has been arrested by the FBI and had their site seized.