This is an extended newsletter, so it may be truncated towards the end of the email. To read the full post, just select the View entire message hyperlink at the bottom of the email or Open in Browser!
Admin access on Apache Superset through default keys
Horizon3 have their thinking cap on this week, and report that the open-source data visualisation & exploration tool has been - and still is, in many cases - using a default Flask Secret Key to sign authentication cookies.
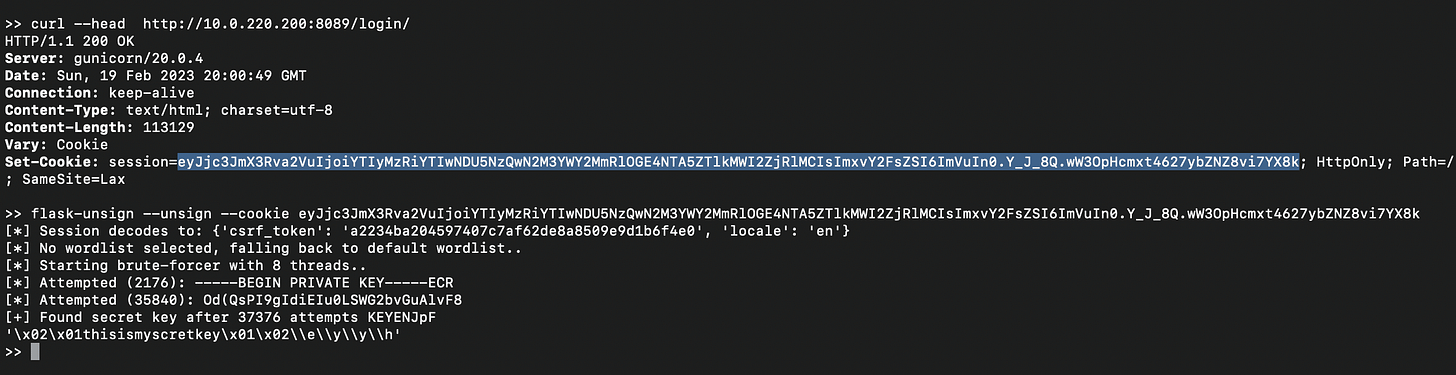
This means that an attacker can simply forge session cookies using this known, default key - allowing them to access the servers with administrative privileges.
While the Superset team have attempted to remediate this by preventing a server from booting when configured with the default secret key, this measure isn’t present on instances run through docker-compose or installed via a helm template.
Get your skates on
Unbelievably, despite initially reporting this flaw to Superset in October 2021, Horizon3 found that 67% of instances - 3,176, to be precise - were still using one of the four default keys.
Horizon3 have published a script which can help confirm if your server is vulnerable by leveraging the flask-unsign toolkit to check if it uses one of the known default keys. If confirmed, follow these instructions to generate and configure the use of a unique secret key.
Spot the Skimmer
Researchers over at Malwarebytes have uncovered a skimmer which is as complex as it is convincing, and was found installed on compromised sites running the Magecart eCommerce platform.
The skimmer, known as Kritec, inserts a crafted modal element in the checkout page that disables and greys out the background - much like you’d see in a legitimate checkout process - and prompts the user for their credit card information.
It’s been crafted specifically to match the aesthetics of the compromised website, and is heavily obfuscated to hinder analysis. Once the victim enters their card details, a fake progress wheel and error message is presented before redirecting the user to the real checkout page.
Take a look and see if you reckon this is something you’d fall for - or be able to spot at a glance:
Other Reporting
Palo Alto have released an update on recent espionage operations conducted by Granite Typhoon (formerly GALLIUM) - a Chinese threat group who were spotted using a new variant of the PingPull backdoor, as well as a simpler malware dubbed Sword2033. The Linux backdoors were used in recent attacks which have expanded their scope to target financial institutions and government entities;
An espionage-motivated threat group tracked by ESET researchers as Evasive Panda were identified to have targeted users in mainland China to deliver their MgBot backdoor via infected updates for the Chinese-developed Tencent QQ software;
Researchers from Kaspersky have shared their findings on a group tracked since September 2021 dubbed Tomiris, who they believe to be linked to the Turla Group and seek to pilfer internal documents from “government and diplomatic entities in the Commonwealth of Independent States (CIS)”;
Checkpoint have published analysis of Educated Manticore, an Iran-aligned actor with overlaps with Mint Sandstorm (formerly PHOSPHORUS) and an interest in Israeli organisations. The group has adopted the use of disk images in their infection chains and employed an improved version of their PowerLess payload;
🔥Withsecure analysts have flagged two instances of in-the-wild exploitation of a recently patched vulnerability in the Veeam Backup & Replication software (CVE-2023-27532) by actors employing tools and techniques attributed to the FIN7 threat group. Make sure you’re patched - or at least don’t have the vulnerable port exposed to the internet;
Cyware have reported that operators of the Play ransomware strain have adopted two new tools in operations - Grixba, a network scanner and information stealer; and “VSS Copying Tool”, used to steal files from existing VSS files prior to encryption;
SOCRadar have published an updated profile for LockBit 3.0, with recent stats on the distribution of victimology by geography and industry, and more;
Trend Micro has reported that the ViperSoftX infostealer has gotten a facelift, targeting additional cryptocurrency wallets, adding anti-detection and analysis measures, and appears to now be targeting KeePass and 1Password credential vaults;
🔥Researchers at Elastic Labs have examined an new infostealer they’ve dubbed LOBSHOT - believed to be used by the TA505 threat group - which is delivered via Google Ads and spawns a hVNC session for the attacker to connect to;
Another report released by Trend Micro last week looks at Rapture, a new Themida-packed ransomware strain which shares technical similarities to the Paradise ransomware family;
Google have gone after the infrastructure of the Cryptbot infostealer by filing law suits against several distributors of the malware across the world. The infostealer was estimated to have impacted some 670,000 computers, and would be disrupted through takedowns of C2 domains.
PaperCut mass-exploitation aided by public PoC exploit
The creators of the PaperCut print management software warned on April 19th that a pair of critical vulnerabilities - which they’d released patches for back in March - were being exploited-in-the-wild by an undisclosed set of actors.
Earlier this week, Microsoft unveiled Lace Tempest (formerly tracked as DEV-0950) as one of the known actors abusing this vulnerability - in their case, to deliver CL0P ransomware through an attack chain that featured a PowerShell downloader, the TrueBot malware, and the Cobalt Strike framework.
The group has previous form targeting unpatched software to achieve their objectives, having leveraged the recent GoAnywhere vulnerabilities and Raspberry Robin malware to deliver ransomware.
Notably, Microsoft went on to note there were “other attacks also exploiting these vulnerabilities, including intrusions leading to LockBit deployment.”
The true scale of abuse of these vulnerabilities is clearly still being discovered, but already it’s highlighted - on the back of the recent GoAnywhere exploit bonanza by the CL0P ransomware gang - a potential developing interest in ransomware affiliates for leveraging emerging vulnerabilities en masse to conduct campaigns.
Why stem the tide when you can ride it
Having apparently decided the proverbial cat was out of the bag, Horizon3 researchers released a working PoC exploit for CVE-2023-27350 - the CVSS 9.8 vulnerability in the PaperCut MF/NG print management software - early last week.

While actors may already be exploiting the vulnerability, it’s hard to argue that releasing a working PoC exploit is going to do more than let other attackers - who otherwise didn’t have a way to exploit the vulnerability - get in on the action.
Even now, there appear to be approximately 757 internet-exposed PaperCut servers which are listening on the default web management port of 9191:

So, yeah. Happy Monday, I guess?
Other Vulnerabilities
Potential privileged command injection on IBM AIX platforms
Two vulnerabilities discovered by Cisco researchers in the IBM AIX Unix platform have been patched, which could have been “exploited to inject commands and logs into targeted systems with elevated privileges.”
Pwn2Own bugs patched in VMWare Workstation & Fusion
VMWare have released updates to address four vulnerabilities with impacts ranging from information disclosure to code execution - two of which were uncovered at Pwn2Own Vancouver this year and netted researchers a cool $80k.
Cisco patch remote XSS bug in server management software
Cisco have issued patches for CVE-2023-20060, a bug in their Prime Collaboration Deployment (PCD) software that would allow remote XSS attacks through sending a crafted link to a user, culminating in arbitrary code execution.
Offensive
DeepSecrets - a tool that supports scanning over 500 languages and formats for unsecured secrets;
🔥Bin-Finder - A standalone tool to help detect processes with/without specific DLLs loaded, e.g. to identify EDR exception policies, or resolve the PID of particular processes such as lsass.
Defensive
🔥This article by Immersive Labs is a fantastic deep dive into Sliver C2 - how the implant and C2 channels work, and how to detect them;
🔥This post is an excellent and exhaustive write-up demonstrating how to emulate and detect four different variants on the PsExec tool; its implementation in the Metasploit and Sliver C2 frameworks, and how an attacker might be able to bypass these detections;
🔥Permiso have published an interesting blog looking at how attackers could leverage AWS’ Simple Notification Service (SNS) to conduct Smishing;
This post examines blocking options for macro-enabled documents, how to circumvent it, and what this means for defenders who think they’re protected by only allowing signed macros;
Early last week, VirusTotal released Code Insight - an LLM-trained tool that examines and explains the behaviour of suspicious scripts. Naturally, within a few hours someone had figured out how to trick it into saying a submitted script creates puppies - which aren’t malicious, and therefore the script isn’t malicious. Good news, guys - SkyNet’s still a whiles away, I think;
🔥If you’re a SentinelOne customer, you’ll be glad to know they’ve partnered with the PySIGMA project to support the automated conversion of Sigma rules to SentinelOne Deep Visibility queries;
Check out this detailed teardown of the Aurora Stealer builder, as well as a previous version which helps highlight improvements to the platform since late 2022;
🔥Use this query to cross-reference DriverLoad events in Windows Defender against a live list of Living-off-the-Land Driver hashes, pulled from the LOLDriver project at loldrivers.io;
For the TI nerds among us, Mitre has officially unveiled ATT&CK v13 - check out the changes here;
🔥Well this is awkward - it turns out the US Department of Justice, along with Microsoft and Mandiant investigators, actually stumbled upon the SolarWinds breach six months prior when they detected - but then dismissed - anomalous activity on a trial instance of the Orion software they were evaluating at the time;
The Director of the FBI has told lawmakers a statistic that’s both surprising…and also not that surprising when you think about it - that “Chinese hackers […] outnumber FBI Cyber personnel by at least 50 to 1” - as the Bureau bids for an additional 192 staff for the next financial year;
The head of the Canadian Centre for Cyber Security (CCCS) has sounded the alarm on the threat of Russian hacktivism to Canada’s pipelines, citing claims by members of the Zarya hacking group that they could "increase valve pressure, disable alarms, and initiate an emergency shutdown of an unspecified gas distribution station” located in Canada;
gpt4free - Lets anyone use gpt4 without an API key. It also has a template chatbot that has access to gpt4, searches the internet, and bypasses OpenAI safety censors.









